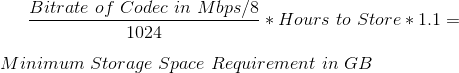We are using Acunetix’s Web Vulnerability Scanner to help us automatically test web applications for SQL injection, cross-site scripting and other vulnerabilities. To scan login protected areas the Web Vulnerability Scanner features the so called Login Sequence Recorder. It basically recordes all the HTTP requests necessary to login and replays them whenever the current user session was terminated.
This works great as long as there is no CAPTCHA and no CSRF token. If any of those two is used we have to manually take action by using another feature called Manual Intervention. It basically opens a web browser window with the current site’s login already preloaded and you are requested to proceed manually until the user session is successfully reestablished. This is quite annoying as you have to re-login several hundred times if the application aggressively terminates user sessions.
With Sikuli we can now automate the scan even with CSRF secured logins. Check out this video to get a rough overview about what Sikuli is all about. We will use it to script the necessary mouse and keyboard actions needed for logging into the web application and execute them everytime the user session is destroyed.
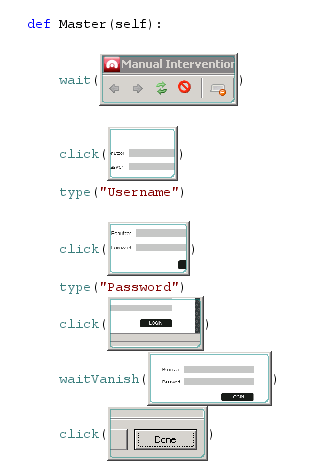
Below is a workflow I used for my last vulnerability scan: At first we wait for the Manual Intervention window to appear and then we click into the username field and type the corresponding name. We repeat this actions for the password. Then we submit the form and wait until the login vanished. Finally, we close the window by clicking Done. Thereby we created a new user session and the scan continues. By using this workflow you can completely automate the login of CSRF protected web applications.