By now, everyone even remotely interested in IT knows that Office Macros are widely abused by The Bad Guys (R) to infect systems with malware. One of the latest Cryptolocker families that applied this trick was the Gandcrab malware:
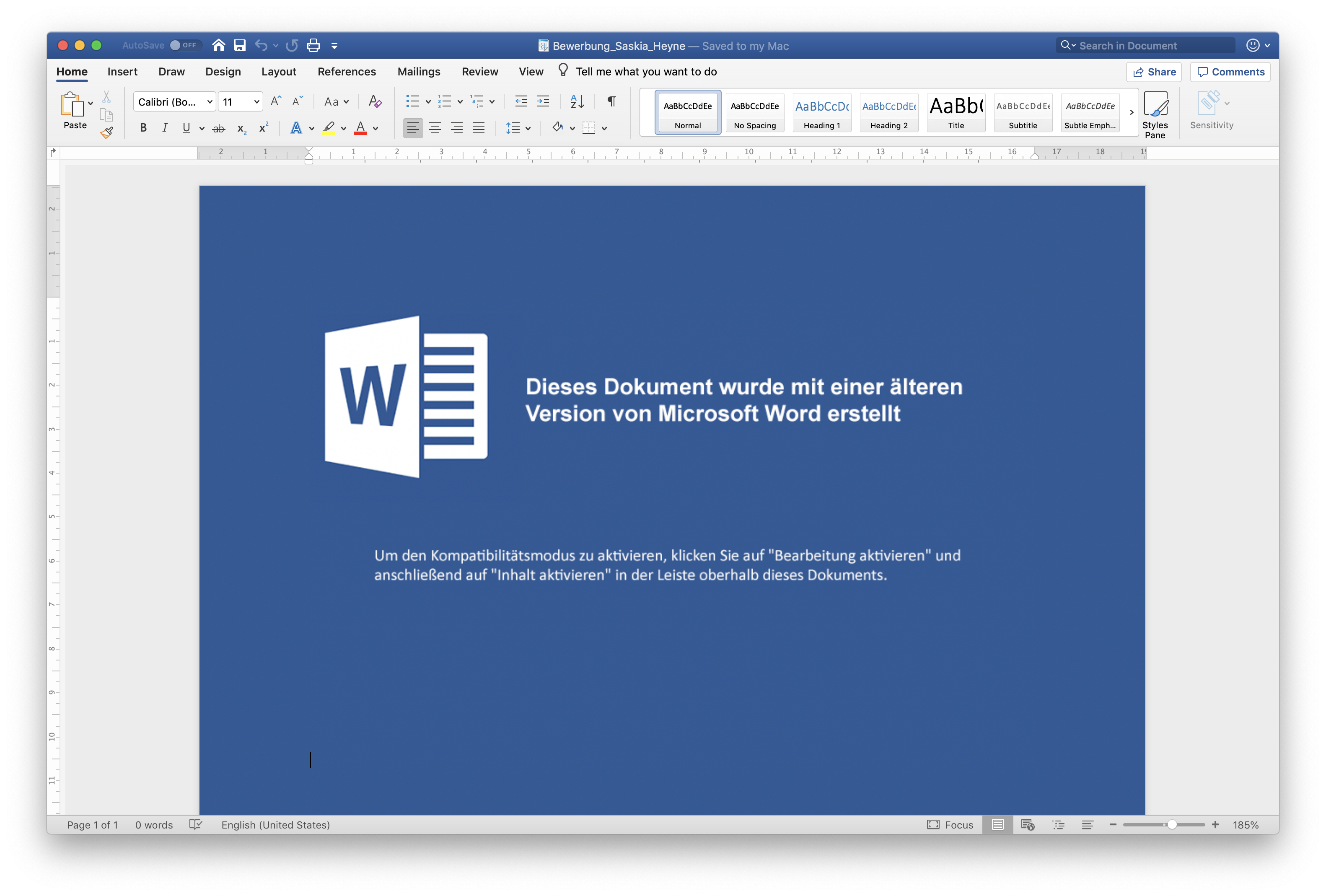
To minimise the risk of a successful infection, I always encourage my clients to block the execution of Office macros. One really great way to do so is the Group Policy “Block macros from running in Office files from the Internet“.
Thereby all end-users are still able to run their internal macros, whereas every document that was downloaded from the web or received by mail is blocked from executing active content.
In the background this is implemented with the help of the Mark-Of-The-Web. This NTFS Alternate Data Stream is set by all modern browsers and mail clients and flags the corresponding file as downloaded from the web.
Did I say: All modern mail clients? Well, almost all I guess… Because Lotus Notes does not set the appropriate flag.
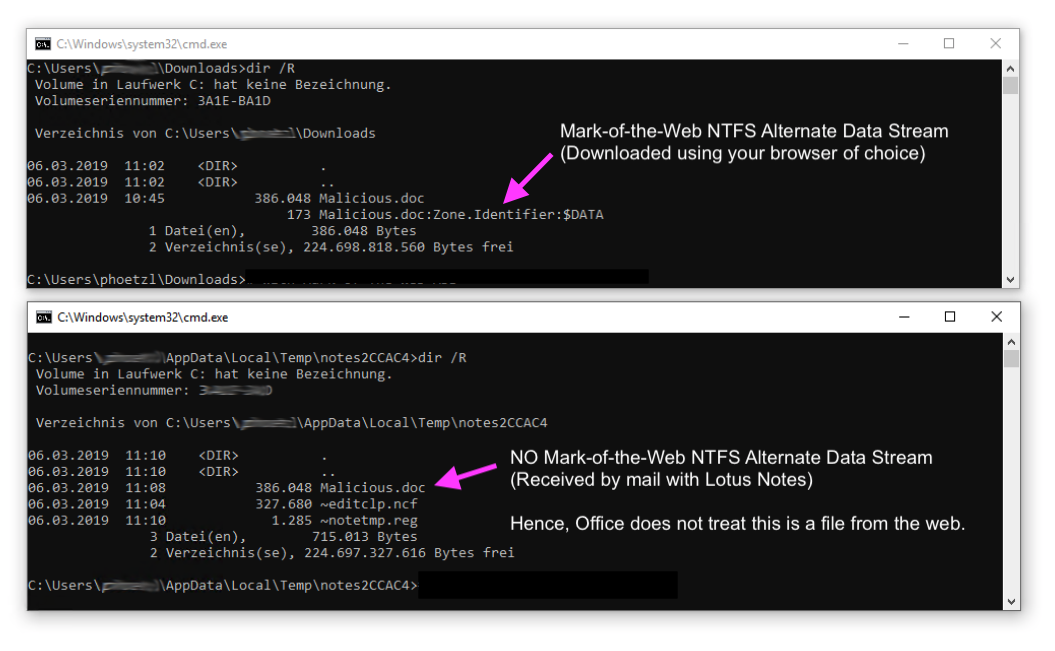
This is pretty bad, because it renders the GPO “Block macros from running in Office files from the Internet” effectively useless. As Microsoft Office has no clue that a file has been downloaded – because the Mark-Of-The-Web is missing – the macros can still be executed…
Unfortunately, I don’t have a workaround… I hope this post at least helps someone else save a few hours of research time.