Just a short disclaimer: Ok, I know… Excel might not be your tools of choice for querying VirusTotal, but there are valid reasons to use it. So, if you think this is a stupid idea – which it might be after all – please let me have my fun…
Recently one of my clients approached me with a very interesting question: Can VirusTotal be queried from Microsoft Excel? The reason for this request was pretty simple: They deployed a new EDR solution which they were still integrating into their SOC workflow. In the meantime they were searching for a graphical way to check all the newly gathered file hashes against VT.

This sounded interesting to me so I dusted off my VBA skills and started some research… As it turns out, there is a fully documented public VirusTotal API and there are libraries to parse the JSON reply from within VBA.
After a few hours of work I can now finally conclude: Yep, it’s totally possible to run VirusTotal queries from within Excel. And yes, I’m providing the XLSM file for free. Just press the big green “Download” button a few lines down. But you should continue reading this post to get the most out of it.
Getting everything ready
So before you can use the tool you have to get a VirusTotal API key. If you already have one, you can skip this step. Luckily this is pretty easy: Just get yourself a Community account and then visit your profile. There you can copy your API key:

Next, download my XLSM VirusTotal checker:
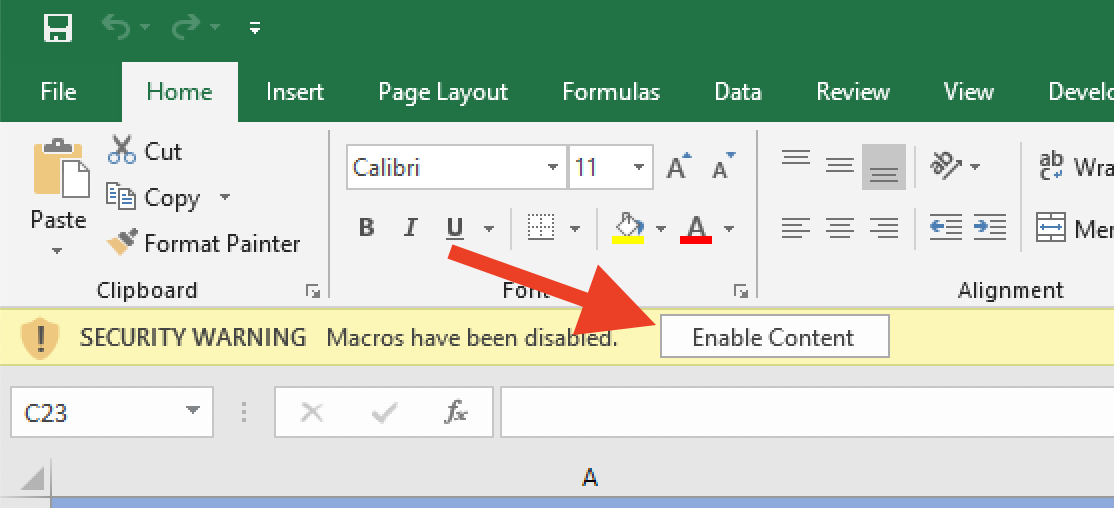
After opening it, you have to accept the Macro execution. Always remember: Don’t execute macros from untrusted sources! (But you know me, I’m a nice guy). Just for reference: this version has only been tested on Windows.
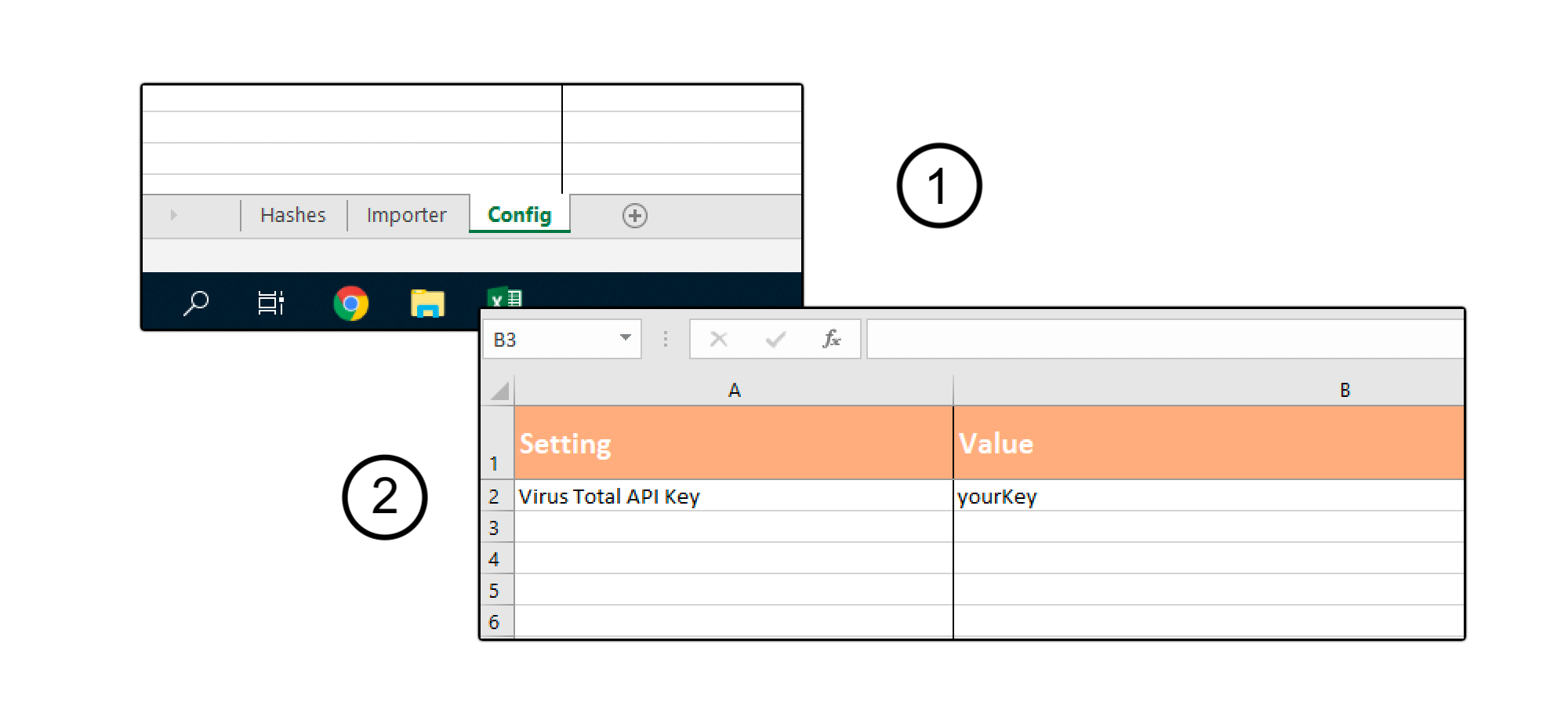
Finally switch to the “Config” table and paste your VirusTotal API key into the corresponding line.
Using the file
Great, you are now ready to rock. The big question is how do you use the file efficiently? Use the Importer! This first script helps you to minimise the number of VirusTotal queries by removing duplicate hashes.
So switch to the Importer table and clear its content. Next, paste your hashes in the given format: the first row is your identifier, the second row the MD5 hash of the file to check. Don’t include empty rows as they are considered the end of the list.
Open the actual importer by clicking the button “Import to Hashes Tables” and start the process using the newly opened window.
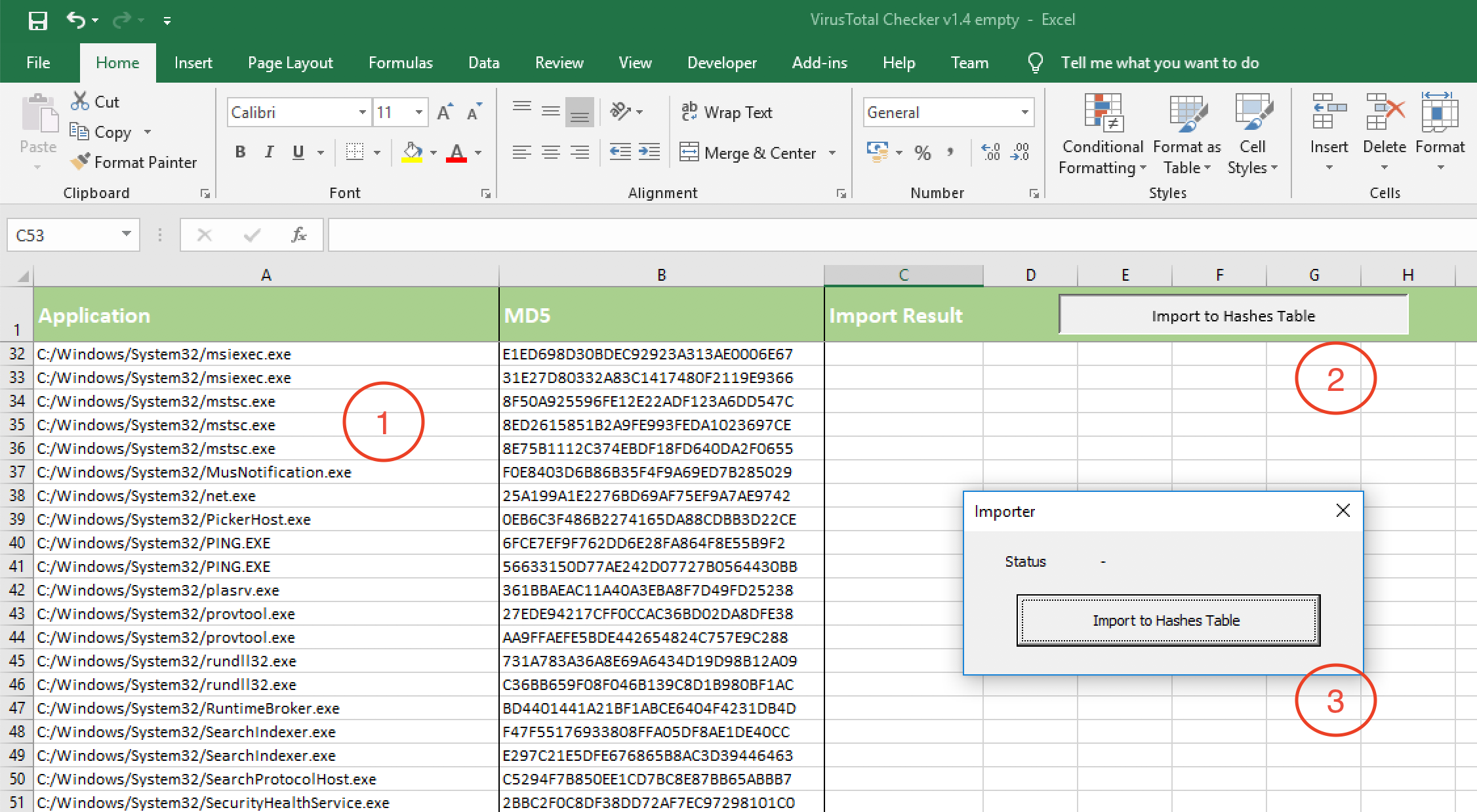
This task now copies all the hashes that are new to the Hashes table. All already existing hashes are simply marked as duplicate.
Finally querying VirusTotal
Thanks for reading that far: But now we are finally ready to query VirusTotal. So, switch over to the Hashes table.
There you should see all your already queried as well as your newly imported hashes. Whenever you want to recheck a given hash, simply empty its result. Please don’t add any empty lines as again they are used to detect the end of the list.
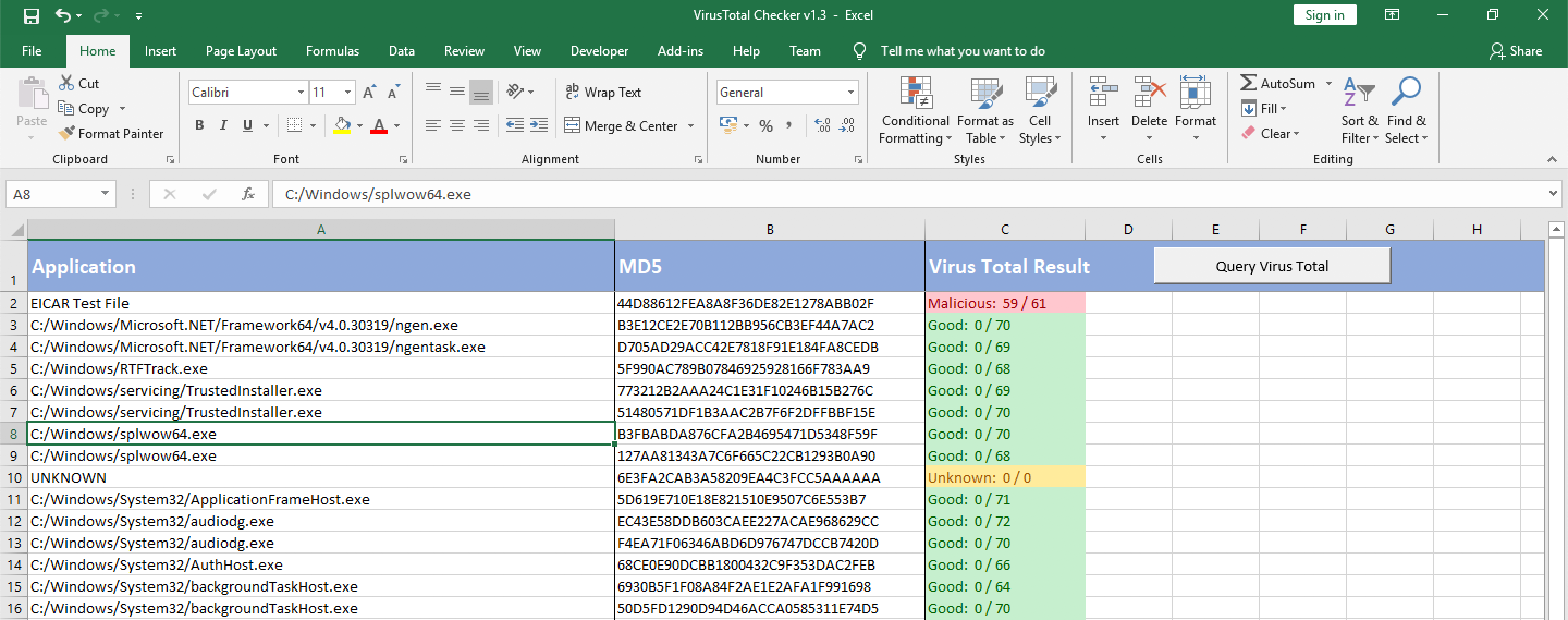
To start the process press the “Query Virus Total” button and the click start.
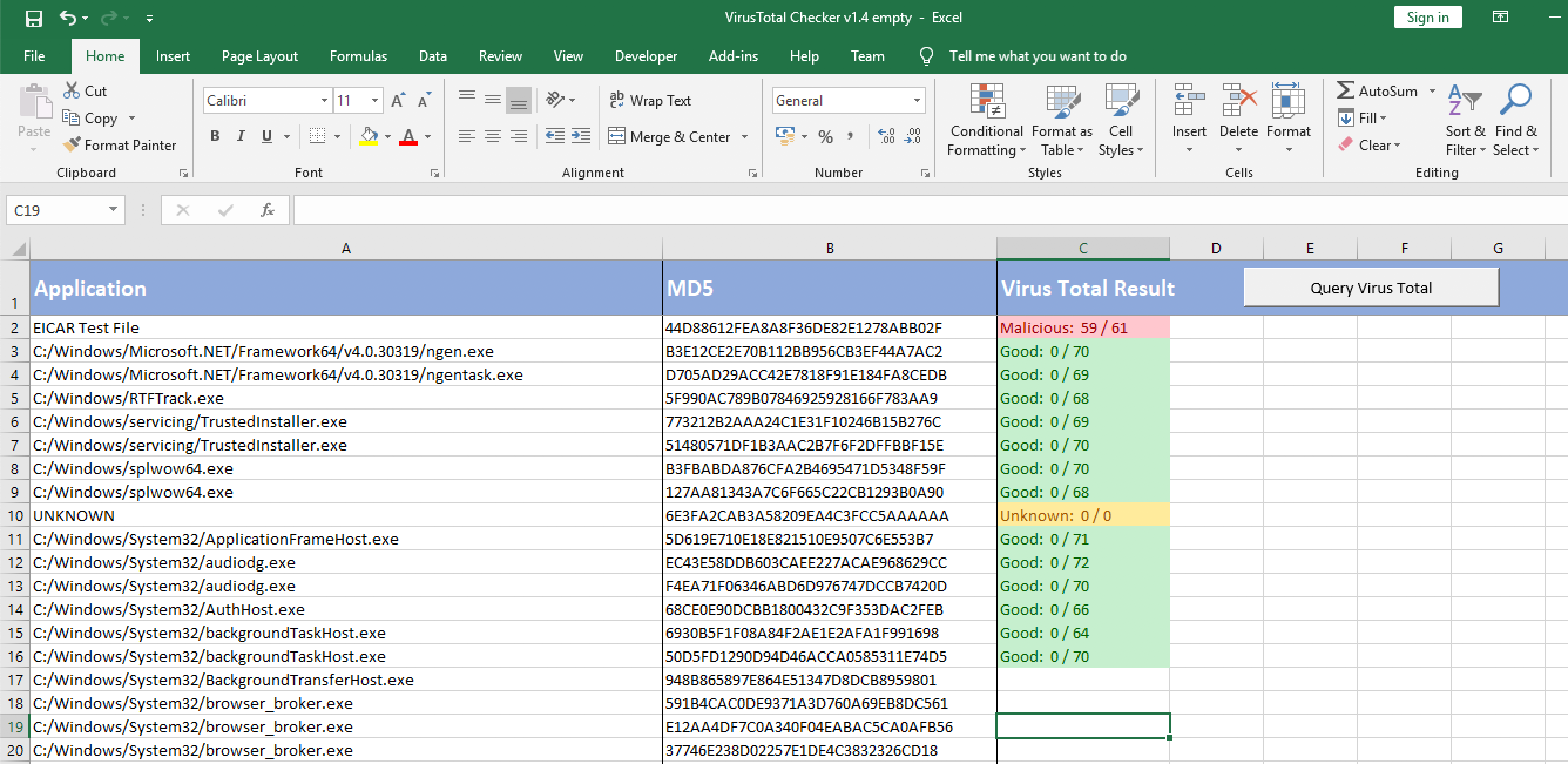
As shown above, new results will appear as the query process continues. There are three possible outputs: Malicious, Unknown and Good. I think they are pretty self explaining. Besides every result the actual detection rate is shown.
For more information you can check out the source code. The interesting part is within the VTQuery module. The rest is just code for gluing everything together.
If you have any further question, please leave a comment below.
