During a recent Incident Response Assignment we at Bee IT Security had to cope with a large Egregor attack. Many of our client’s most critical systems had been encrypted. Luckily, we were able to recover most of them from Offline backups.
However, we were unsure if (I) all encrypted systems had been identified and (II) if no further Egregor activities would trigger. Based on a great article from Cybereason and our own investigations, we knew how the infection was carried out: A Powershell script was used to deploy a malicious DLL to all systems, which was then executed using WMI.
To answer both of our questions, I wrote a small PowerShell script, which checks the current system for the ransom note (I). Additionally the presence of the malicious DLL is checked and logged (II). To hinder further Egregor activity with the same library, a placeholder file is generated and protected with NTFS filesystem permissions (Everyone : Full Control : Deny). A GPO with a Scheduled Task was used to run it on all systems on an hourly base.
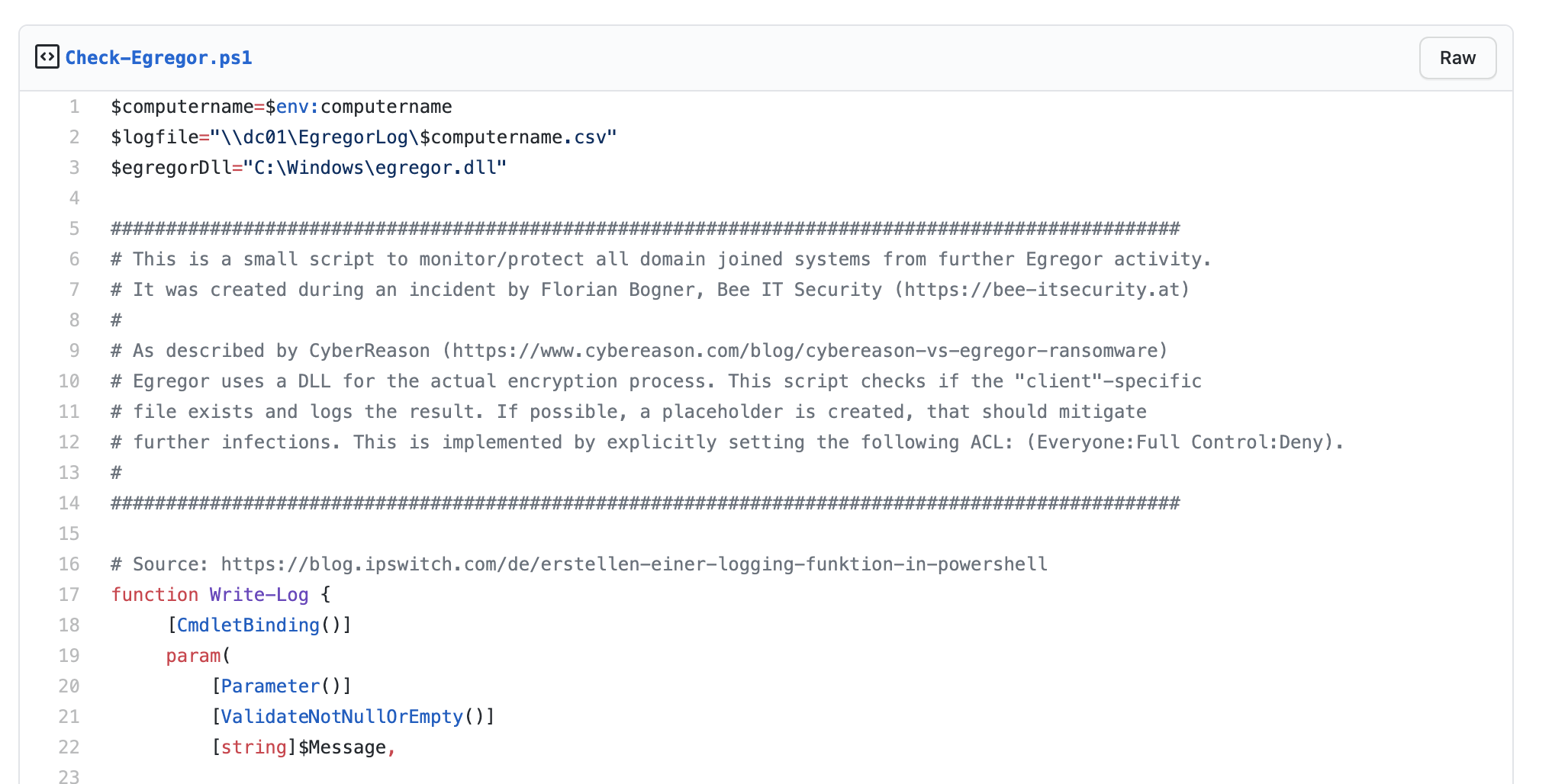
In case you also have the pleasure to meet Egregor, you may find our script handy. You can download it here: https://gist.github.com/fbogner/32fc8b73bcc50287ced91de1883421a9