UPDATE (16.05.2017 @ 21:06): This script should now work for all operating systems up to the current Windows 10 / Server 2016 build 14393.1198
UPDATE (15.05.2017 @ 22:15): There have been several reports that this script did not work on some Windows 2008 and 2016 servers. This was related to Get-HotFix, as it misses some installed updates. Hence, I added a second method to fetch all installed fixes… I guess this should be more stable…
Because of the current situation regarding WannaCry, I needed a simple solution to check if a system has already been patched against all the issues fixed in MS17-010. However, as there are different KB’s for the different operating systems, this is a lot more difficult than I first thought.
Hence, I updated a script I found on the internet so that it can be simply pasted into a PowerShell to check a system.
# Copy and paste this to a Powershell Window to check if MS17-010 has already been installed on this system
function checkForHotFix
{
Write-Host "[*] MS17-010 Checker"
Write-Host "[*] ++++++++++++++++++++++++++++++++++++++++++"
Write-Host "[*] Starting check"
# based on https://www.poweradmin.com/blog/how-to-check-for-ms17-010-and-other-hotfixes/
# and on http://tomtalks.uk/2013/09/list-all-microsoftwindows-updates-with-powershell-sorted-by-kbhotfixid-get-microsoftupdate/
# To find all Hotfixes of a security update copy the page content and
# use http://regexr.com/ with the regex KB[0-9]{7} to extract them
$hotfixes = "KB4013429","KB4012606","KB4013198","KB4012598","KB4012598","KB4012598","KB4012598","KB4012598","KB4012212","KB4012215","KB4012212","KB4012215","KB4012213","KB4012216","KB4012214","KB4012217","KB4012213","KB4012216","KB4012606","KB4013198","KB4013429","KB4013429","KB4016871", "KB4019472"
Write-Host "[*] Querying installed HotFixes using method 1"
$wu = new-object -com “Microsoft.Update.Searcher”
$totalupdates = $wu.GetTotalHistoryCount()
$all = $wu.QueryHistory(0,$totalupdates)
# Define a new array to gather output
$UpdateCollection= @()
Foreach ($update in $all)
{
$string = $update.title
$Regex = “KB\d*”
$KB = $string | Select-String -Pattern $regex | Select-Object { $_.Matches }
$output = New-Object -TypeName PSobject
$output | add-member NoteProperty “HotFixID” -value $KB.‘ $_.Matches ‘.Value
$output | add-member NoteProperty “Title” -value $string
$UpdateCollection += $output
}
Write-Host "[*] Querying installed HotFixes using method 2"
Foreach ($hotfix in Get-Hotfix)
{
$output = New-Object -TypeName PSobject
$output | add-member NoteProperty “HotFixID” -value $hotfix.HotFixID
$output | add-member NoteProperty “Title” -value $hotfix.Description
$UpdateCollection += $output
}
Write-Host "[*] Check if any suitable HotFix was found"
if ($UpdateCollection | Where-Object {$hotfixes -contains $_.HotfixID}) {
$hotfixID = $UpdateCollection | Where-Object {$hotfixes -contains $_.HotfixID} | Select-Object -first 1 "HotFixID"
Write-Host "[+] Hotfix"$hotfixID.HotFixID"installed - System is secure!" -foreground "green"
} else {
Write-Host "[-] No Hotfix found - System vulnerable!" -foreground "red"
}
}
cls
checkForHotFix
# Also copy this comment - This makes it "autorun"
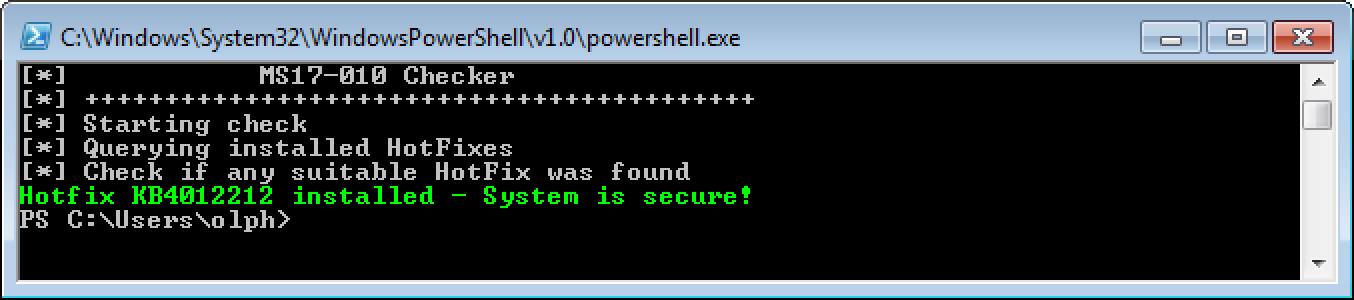
If a system has already been patched it looks like this:
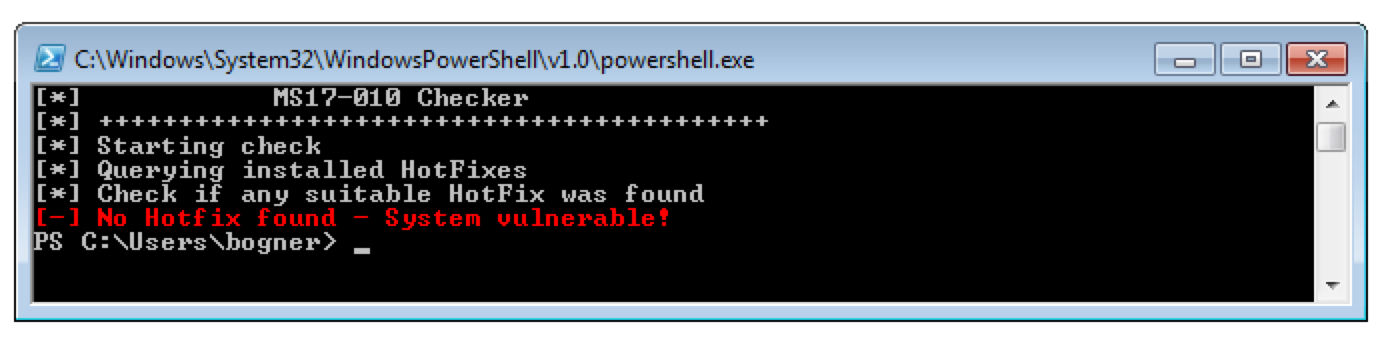
If not, well there is a warning:
Maybe it’s of use for someone else…
Acknowledgment:
- Thanks to Markus for pointing out a missing KB
- Thanks to Hannes for spotting a typing error that caused the script to always report “vulnerable” even on patched systems.
- Thanks to Dustin (see comments) for pointing out another missing KB