This blog post is about a DLL sideloading vulnerability in the 64bit Windows version of Oracle Java. It allows any local user to inject code in Java processes of other users. At the time of writing it has been verified with the latest stable 64bit Java version 1.8.0_101 on both a fully patched Windows 7 and a fully patched Windows 2008R2 operating system. The issue is not triggered by all Java application, however Burp and the 32bit version of Angry IP Scanner have been verified to be vulnerable. I think it depends on the imported frameworks if an application triggers the problem.
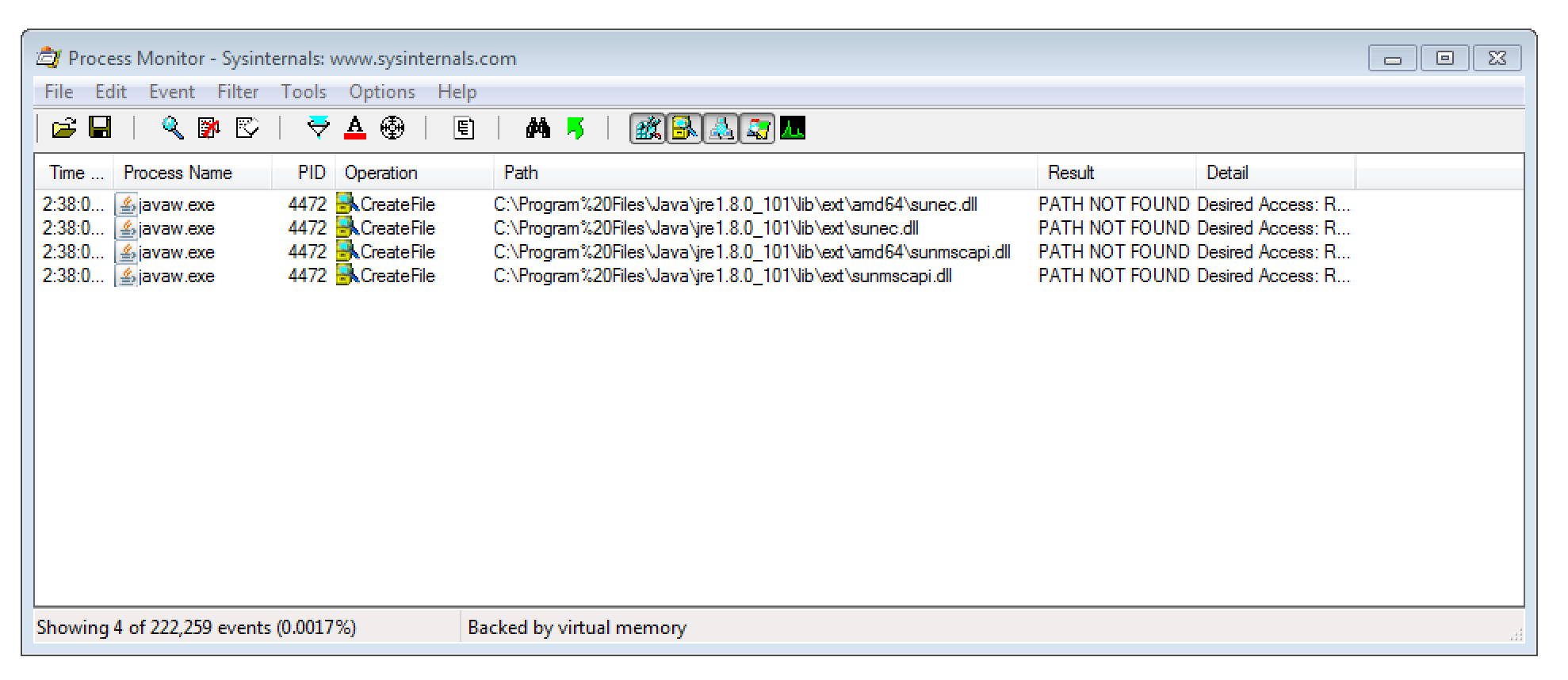
Technically, the issue is that DLLs (namely sunec.dll and sunmscapi.dll) are loaded from the non-existing folder C:\Program%20Files\Java\jre[version]\lib\ext. This is most likely caused by some kind of encoding issue as %20 represents an URL-encoded space.
As any local user is allowed to append new folders to the C: drive’s root, the Program%20Files folder can be created.
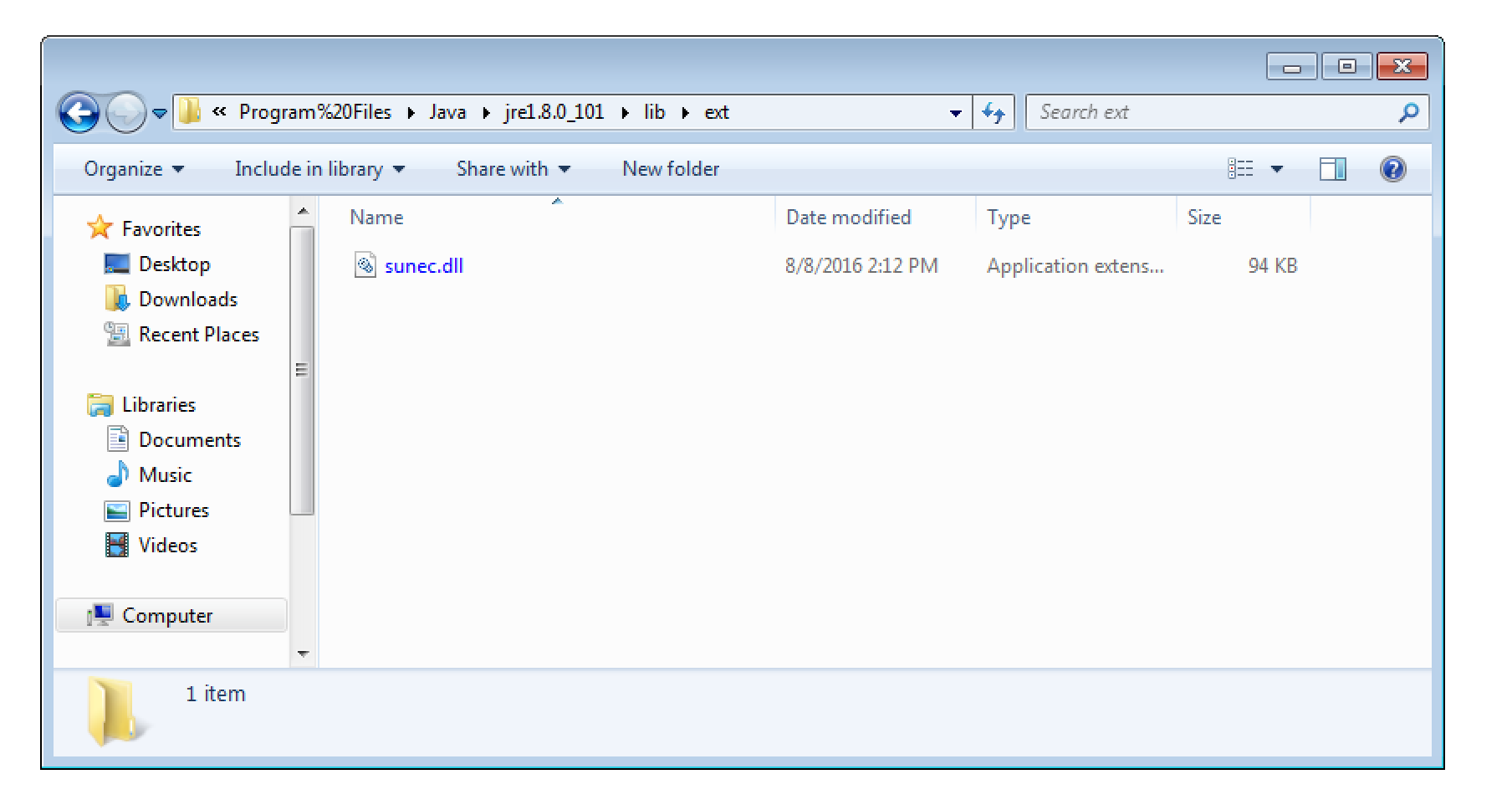
Thereby, any local user can place a malicious DLL into C:\Program%20Files\Java\jre1.8.0_101\lib\ext. I verified this myself by building a simple placeholder DLL.
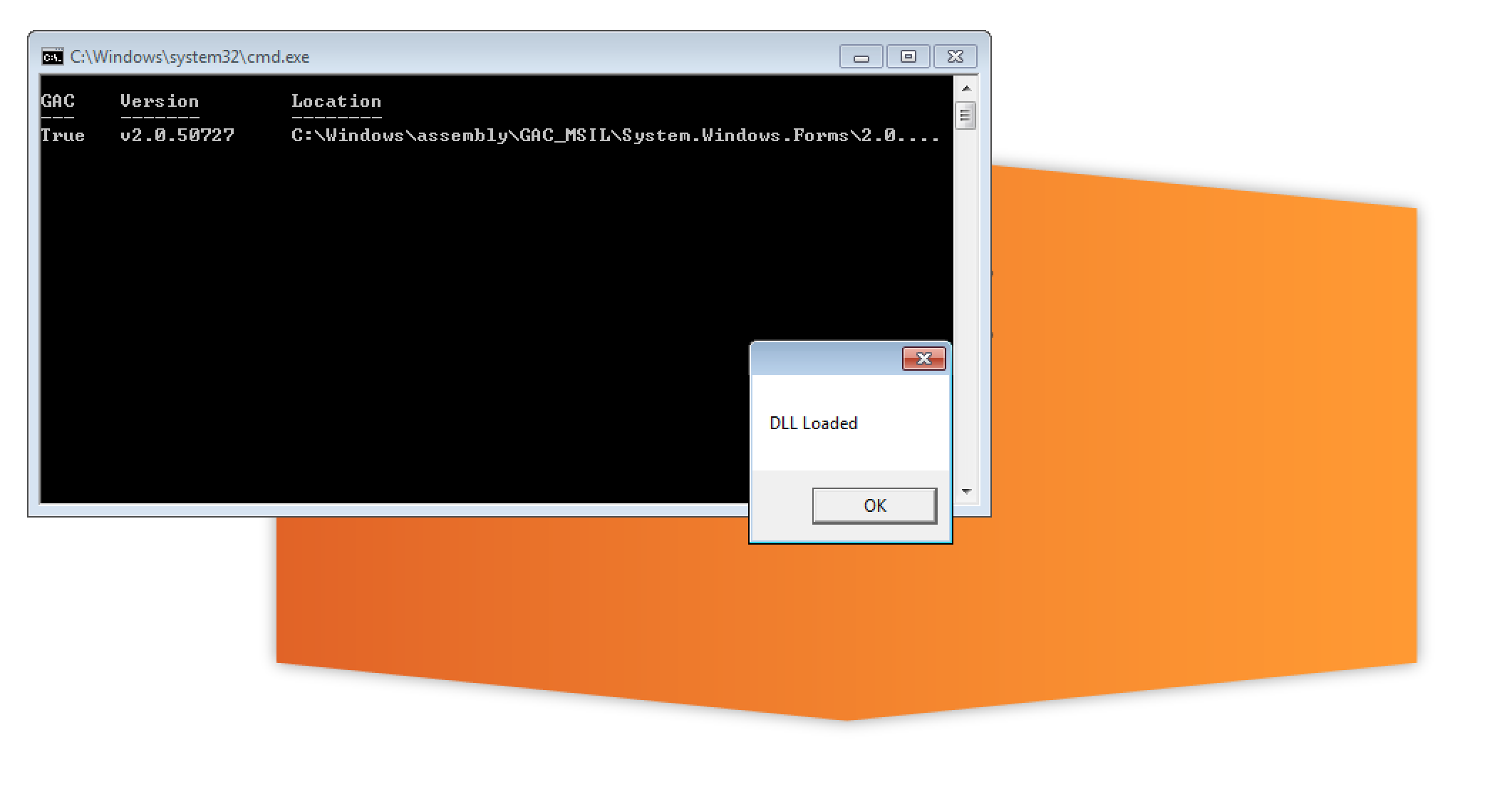
After launching Burp the DLL got loaded and executed. The screenshot below shows the opened dialog.
As the newly created Program%20Files folder is located on the drive’s root, this issue affects any local user. Thereby code can be injected into other user’s Windows sessions. Additionally if any vulnerable Java application is running as privileged application (SYSTEM, local admin, domain admin) this issue can also be used to escalate one’s permissions vertically.
Video
Here is a video illustrating the attack:
Suggested solution
Update to the latest version.
Timeline
- 8.8.2016: The issues have been documented and reported
- 10.8.2016: The issue has been confirmed by the vendor
- 6.12.2016: CVE-2017-3511 has been assigned
- 19.4.2017: Fix release in Oracle’s Critical Patch Update April 2017