Today I want to introduce a small helper tool, namely lsdns. I wrote it as I always struggle to find the correct IP and hostname mappings while writing my pentest reports. lsdns is a small python script that queries a DNS server for a given IP range and outputs the results in a CSV compatible format. In this post I will explain why it is useful to me, where you can get it and how to use it.
 All our pentest reports document the found vulnerabilities, possible mitigation strategies and logically list all affected systems. To help our customers we always try to provide both, the IP address and the corresponding hostname for any computer mentioned. Although this is generally quite easy, it can be quite a pain if you can not access the original DNS server while documenting the findings either because it is only available from the internal company network (and you did not find a vulnerability that allows you to query it externally) or split DNS is used.
All our pentest reports document the found vulnerabilities, possible mitigation strategies and logically list all affected systems. To help our customers we always try to provide both, the IP address and the corresponding hostname for any computer mentioned. Although this is generally quite easy, it can be quite a pain if you can not access the original DNS server while documenting the findings either because it is only available from the internal company network (and you did not find a vulnerability that allows you to query it externally) or split DNS is used.
To at least partially solve this issue for me I wrote lsdns. It is a small application that uses reverse DNS to get all hostnames for a given IP range. The output can be redirected to a CSV file and can be used while writing the report to look up either the hostname or the IP address of a vulnerable system.
Installation
To install it you need to have python2 and the python setuptools already preinstalled. Then you can either clone the git repository or simply download the latest ZIP from GitHub. Before you can use it you have to manually install the dependencies from within the dependencies folder by running the corresponding setup.py scripts. After that you are ready to go.
Usage
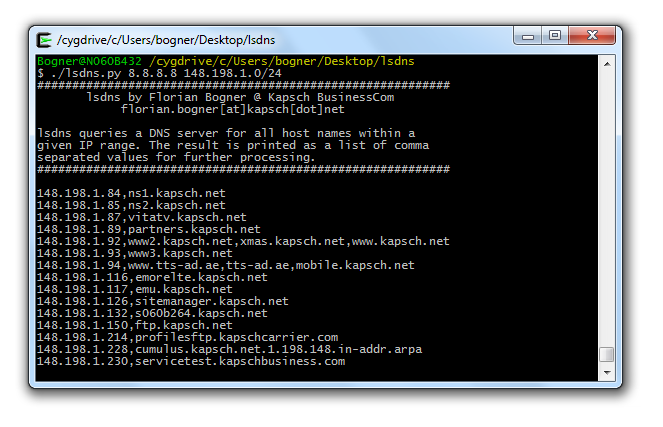
dnsls is a very simple to use command line utility. The following example shows how to do so:
./lsdns.py <dns server to query> <IP address or range> Example: ./lsdns.py 8.8.8.8 148.198.1.0/24
By redirecting stdout to a file a valid CSV file is created. To still give you feedback about the progress a dot is printed for each host. A sample is available here.
I hope someone else also sees a value in dnsls. If so, it is freely available for you under the terms of the MIT licence.